Sex and Compliance on the same website? Who would have thought!?! In our section on the most popular examples of online scam and fraud, we show you cases of the latest attempts to con you and steal your hard-earned money, break down the ploy and show you how to avoid it. Today, we are looking at the Sextortion Scam that is making the rounds and seeks to use your guilty conscience to make you part with your bitcoins. Here is what you need to know and do about it.
The evidence
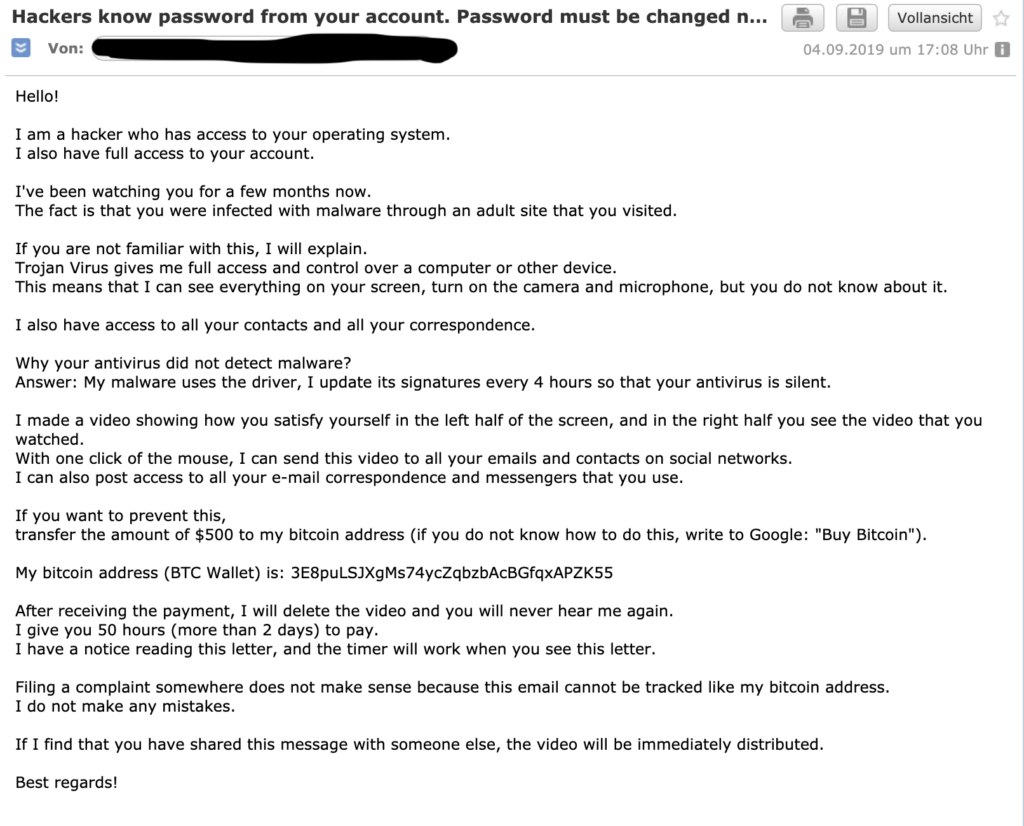
The other day I received an email telling me that my account had been hacked. The funny thing was that it appeared to come from my own e-mail account, i.e. sender and recipient were the same, which immediately got my heart racing:
(I have blackened my actual email address since I already get enough spam – I’m sure you understand)
Luckily, this is the second time I receive this kind of email (God knows who sells my email address over the Internet), so this time round I was less alarmed, but I have to admit that the first one I got a similar email that a few weeks ago I’ve been fairly spooked.
Don’t get me wrong. I wasn’t so much concerned about the dirty secrets that might be revealed about me – I’m pretty confident that I didn’t do any of the things I was accused of in the e-mail. The fact that it came from my own e-mail address though got me a little worried. Had they perhaps really hacked my account? What else did they retrieve from my computer?
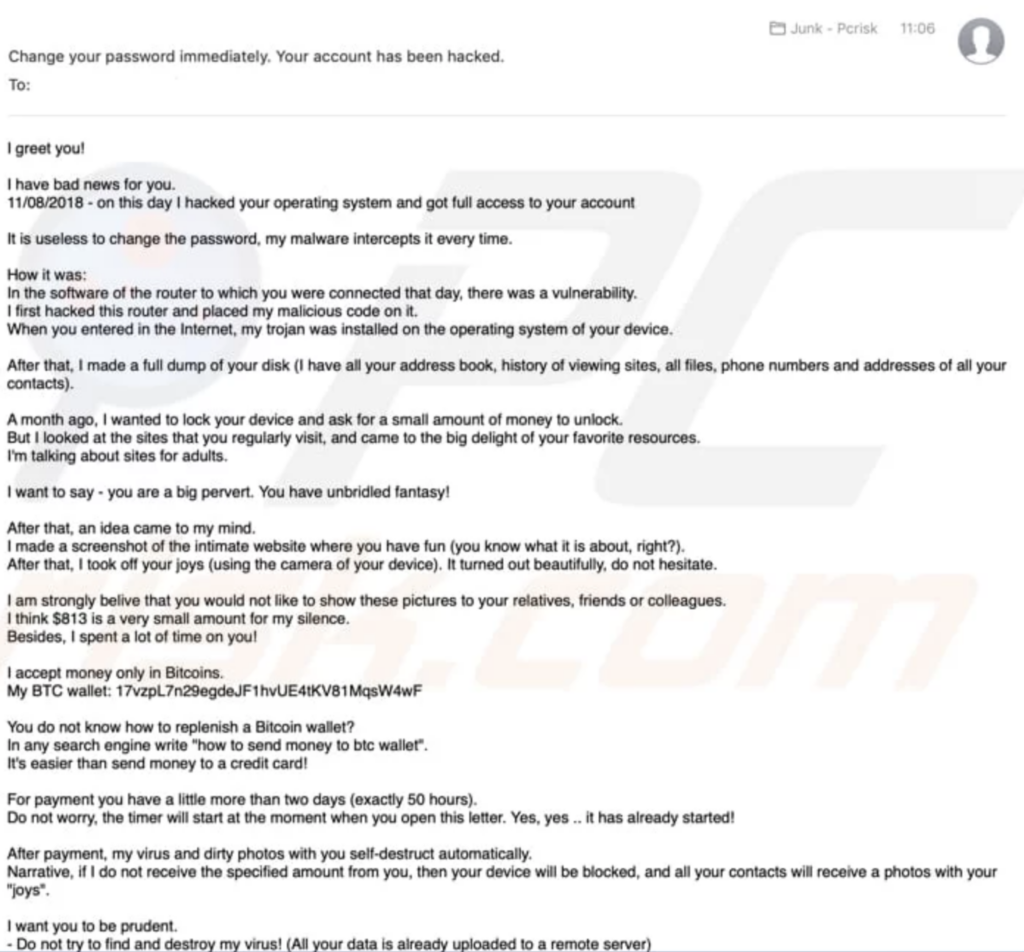
As always, it helps to keep calm and do a bit of research. A simple Google search revealed that I unsurprisingly wasn’t the only one that had received this kind of threat. Here is an example similar to the first e-mail I had received courtesy of PCRisk:
How it works
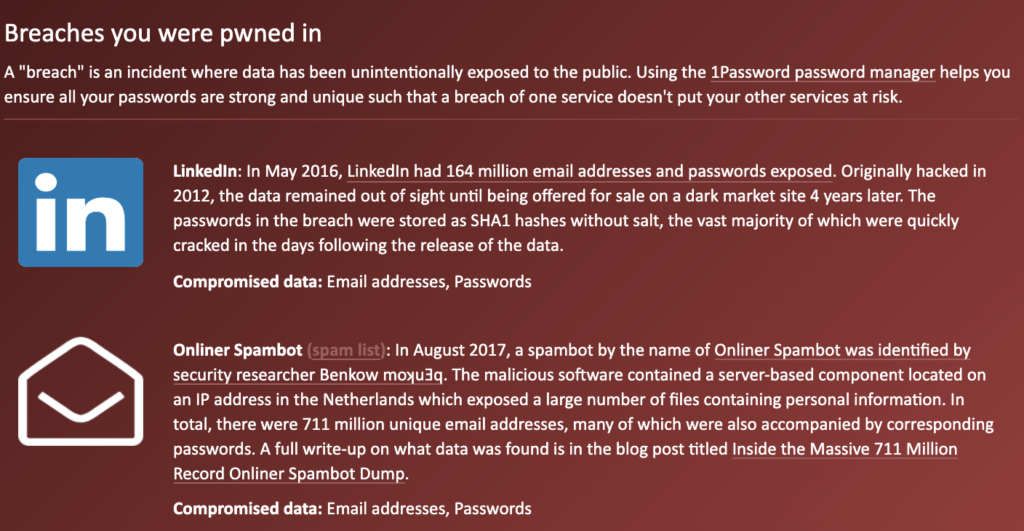
And there are quite a few of these cases out there as the search results show and since the number of data breaches steadily increases, it is not surprising that my email address, too, ended up in the hands of some criminals. If you want to check the status of your account simply head over to Have I Been Pwned. As you can see from my check below, my account was possibly involved in data breaches where close to a billion email been unintentionally exposed to the public and in consequence to the nice person that sends me these messages.
Fortunately, it is very unlikely that in this particular case someone managed to hack your computer and record your activity. If you are mindful and take a couple of precautions to protect the security of your account(s), chances are that they don’t even have the password you are using for this account. Still, how do they manage to make it look like it came from my own address?
Well, as it turns out, most e-mail software does not even verify who has actually sent an email address, but simply transmits what the sender enters in terms of information. So, even I could send an email to someone and just by adding the information of the person I pretend to be, e.g. bill@microsoft.com and the recipient might be inclined to think I’m Bill Gates as explained in detail on How-to-Geek.
Of course, you can easily get more information about the true origin of an email – simply view the source information in your email software, but that is of course seldomly done as we all have to rely on the power of our spam filters in order not to drown in a flood of junk mails in most cases.
What can you do about it though?
While it is difficult to entirely eradicate this problem, there are four steps to should provide some relief.
1) To start with, stay calm!
Even if you really have been doing what these people accuse you of, there is always time to do a quick search and don’t just send Bitcoins to some address since there is no guarantee that you’re off the hook.
2) Always remember to be vigilant
Don’t open attachments or links in emails from people you don’t know and even from those among your contacts look out for suspicious things like a blank email with only a zip-file to extract.
3) Use secure passwords and/or multi-factor authentication
Seriously, “password” won’t do anymore, but even more sophisticated passwords don’t take long to break – have a look here to check how long a bruteforce attack would take.
4) Support the system
Help your email software by marking messages that have managed to slip through as spam or junk. These systems learn from behavior and you can make them better by telling what is what. They also use public data, so if you got a phishing email, you can forward it to organizations like the FTC at spam@uce.gov or to the Anti-Phishing Working Group at reportphishing@apwg.org.
Does the scam actually work?
Since these emails came with precise instructions where to pay the money to in the form of a Bitcoin address, you can, of course, use this information to see how many people fall for it.
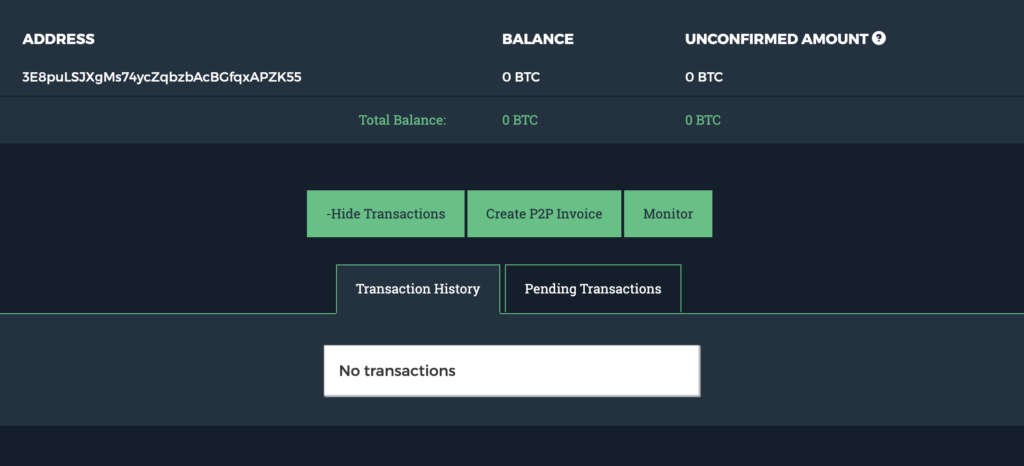
Simply using a service that provides information on the account balance of a Bitcoin balance I could tell that in my case these crooks hadn’t managed to fool anyone yet. Zero balance and no transactions, however, only means that the address that was used this time hadn’t received any payments yet. Going through the various cases of the sextortion scam shows the amount of Bitcoin wallets being used, so it’s difficult to measure the actual success rate. One can only hope it’s not very high.