The growing use of digital infrastructure has opened many avenues for cyberattacks and exploitation. The ever-increasing data breaches across systems worldwide are a testament to the presence of these vulnerabilities. To avoid these data breaches and their resultant financial and reputational loss, organizations are using a combination of strategies to secure their systems.
Below are some of the best PTaaS platforms available today:
- Pentest-Tools.com A web-based service that helps security teams discover, exploit, and report the vulnerabilities present in an application. It saves time and effort while speeding up performance.
- CrowdStrike A sophisticated penetration testing platform that identifies and mitigates vulnerabilities across your entire IT infrastructure. It also reduces your organization’s attack surface area.
- Intruder An automated penetration testing platform that identifies security weaknesses in your infrastructure to help prevent a data breach.
- Astra Pentest An advanced pentest platform used to monitor vulnerabilities continuously. It is ideal for modern engineering teams who need complete control and visibility.
- BreachLock An attack surface discovery and penetration testing tool that identifies and mitigates risks.
One such testing strategy is Pen Testing as a Service (PTaaS). Read on as we discuss what is pen testing, its benefits for your organization, and the five best platforms today.
What is Penetration Testing?
A penetration test or pen test, in short, is a cybersecurity strategy for identifying the vulnerabilities in your system. It is a simulated attack performed by experts to evaluate the security of a system from the perspective of cyberattackers. In other words, a pentest is carried out by ethical hackers who deliberately attack a network or system to show the organization its potential vulnerabilities, and what it needs to fix.
Next, let’s see how this testing works.
How Does Penetration Testing Work?
The exact working of a pen test depends on the expert executing it and the tools involved. Here’s a look at the broad steps involved.
Step 1: Planning and Preparation
In the first step, testers and the organization define the scope of the testing process. They set the objectives, decide which areas should be tested, and what methods and tools to use. During this stage, organizations also get the necessary permissions and information for the testers.
Step 2: Reconnaissance
During this phase, the test collects information about the organization’s infrastructure and systems. Using this information, they identify the potential vulnerabilities and how they can attack the organization. Sometimes, testers also use automated scans to analyze ports and configurations for potential vulnerabilities.
Step 3: Gaining Access
Next, the testers try to gain access to the system using the information they gathered in the previous step. This process could include techniques like password cracking, social engineering tactics, and more. The testers think like hackers and try to gain access to the system. Once inside, they carry out attacks or move through, based on the objectives.
Step 4: Analysis and Reporting
During the entire attack, the testers keep detailed records of their actions. This information is then analyzed and accordingly, the tester generates a report detailing the vulnerabilities. Also, the testers can provide recommendations based on their testing experience.
Step 5: Remediation
Organizations can plan for remediating the vulnerabilities based on the tester’s reports. Security teams prioritize and address issues before they are exploited by hackers.
The above steps show how penetration testing can help organizations. Next, let’s take a detailed look into why organizations must use pen testing regularly to beef up their security.
Benefits of a Pentest
Penetration testing helps an organization understand its security gaps and determine the robustness of its security controls. Also, it is used to evaluate how well an organization is prepared to handle cyberattacks.
Does it have a response plan? How effective is the plan? Can it mitigate the attack? You can get answers to these questions with Pentest.
Here are other benefits of penetration testing:
- Makes it easy to prioritize vulnerabilities, so you can allocate resources accordingly.
- Reduces the chances for hackers to exploit your weaknesses.
- Identifies areas that need improvement from a security perspective.
- Avoids costly data breaches and the resulting financial and reputational losses.
- Reduces downtime due to cyberattacks.
- Helps meet compliance requirements.
- Enhances incident response capabilities.
- Provides a third-party perspective to your security systems.
- It can be a tool for training your employees and increasing their awareness of cybersecurity.
- Increases customer and investor confidence in your business.
- Optimizes your spending.
Now that you know the benefits of a pentest, note that it often requires sophisticated tools for implementation and analysis. Over the years, these tools have evolved to reflect the technological advancements in this space. Today, we have a mix of traditional and cloud-based tools, each with its unique advantages and disadvantages.
Traditional Pen Testing vs. Pen Testing as a Service (PTaaS)
Penetration testing tools come in many forms to meet the needs of different organizations. Testers use traditional testing tools to evaluate the security of specific areas or applications in your IT infrastructure.
However, they come with a set of limitations. One of the primary drawbacks of these traditional pen-testing tools is that they rely largely on the ability of the hackers to execute the tests. Sometimes, more than one hacker is required to test a system, and the differences in skills and competencies can also hinder the outcome of the results.
Penetration Testing as a Service (PTaaS), on the other hand, is a cloud-based approach designed to overcome the limitations of traditional pen testing platforms. These tools come with an intuitive user interface that supports real-time collaboration among the testers.
Moreover, the robust integrations of PTaaS coupled with its access to unlimited resources make it a more powerful option for penetration testers. Also, these toolkits are less reliant on the individual skills of a tester and can produce similar outcomes because of the strength in technology and the cloud-based analysis.
Due to these advantages of PTaaS over traditional pen testing platforms, more pen testers and organizations are moving towards PTaaS.
Our Methodology
To identify the above best picks, we evaluated the tools on the following criteria:
- Scalable to meet the growing touchpoints of an organization.
- Ability to gather data from different sources and analyze them.
- Lower Total Cost of Ownership (TCO).
- Effective reporting.
- Availability of a wide range of tools to identify and evaluate different threats.
- Extensive identification of vulnerabilities
- Seamless integration with existing infrastructure.
Pen Testing as a Service (PTaaS) Platforms
Let’s now see the features of each tool to help you identify the best fit for your needs.
1. Pentest-Tools.com
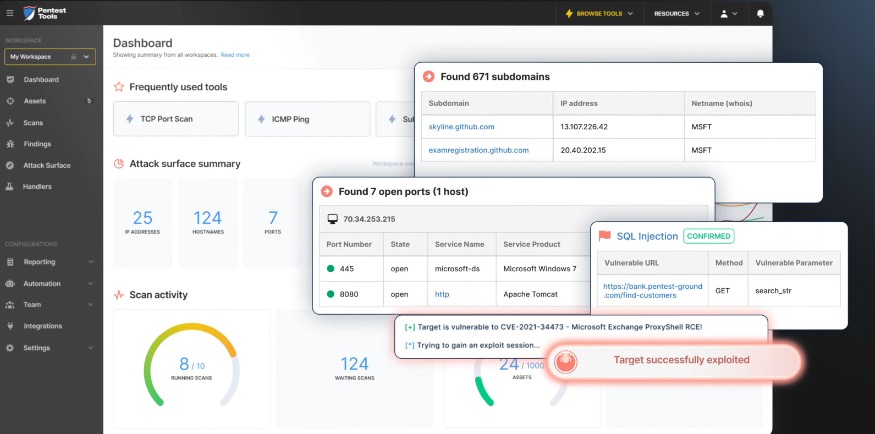
Pentest-Tools.com is built by a group of expert penetration testers to speed up the common steps involved in any penetration testing process. It comes with more than 20 built-in tools that can handle all aspects of penetration testing to give the desired insights.
Source: Pentest-Tools.com
Here are Pentest-Tools.com’s features.
Attack Surface Mapping
Pentest-Tools.com evaluates the attack surface of your network, device, or application, including the subdomains, open ports, running services, and more. It uses a combination of tools like URL Fuzzer, Subdomain Finder, and Port Scanner to map web technologies, discover hidden files, and identify any potential vulnerability lurking in the background.
In-depth Scanning
Using a combination of tools like Website Vulnerability Scanner and Network Vulnerability Scanner, Pentest-tools.com can identify common vulnerabilities across your web applications and networks respectively. It works with popular tools like WordPress, Drupal, Sharepoint, Joomla, ProxyShell, Log4Shell, etc., to identify specific security issues. With these tools, you can also find weak credentials to identify the risk of unauthorized access.
Report Generation
An essential part of any penetration testing is the generation of reports that provide all the information your organization needs to take further action. Pentest-Tools.com’s Report Generator module creates reports from your findings, which is estimated to be 50% faster than manual reports. Also, it comes with many Word document templates and a rich library of common findings to create highly readable and insightful reports.
With such extensive features, Pentest-Tools.com can help pen testers identify a wide range of issues without having to install or deploy any tool. Also, its extensive tool options provide a ton of flexibility that goes beyond the skills of an individual tester.
Pros:
- Hassle-free use, as it requires no installation.
- Integrates with identity providers.
- Cloud-based and hence it is device-agnostic.
- Good customer support.
Cons:
- No logging option for scans.
- Limited tutorials and documentation.
2. CrowdStrike
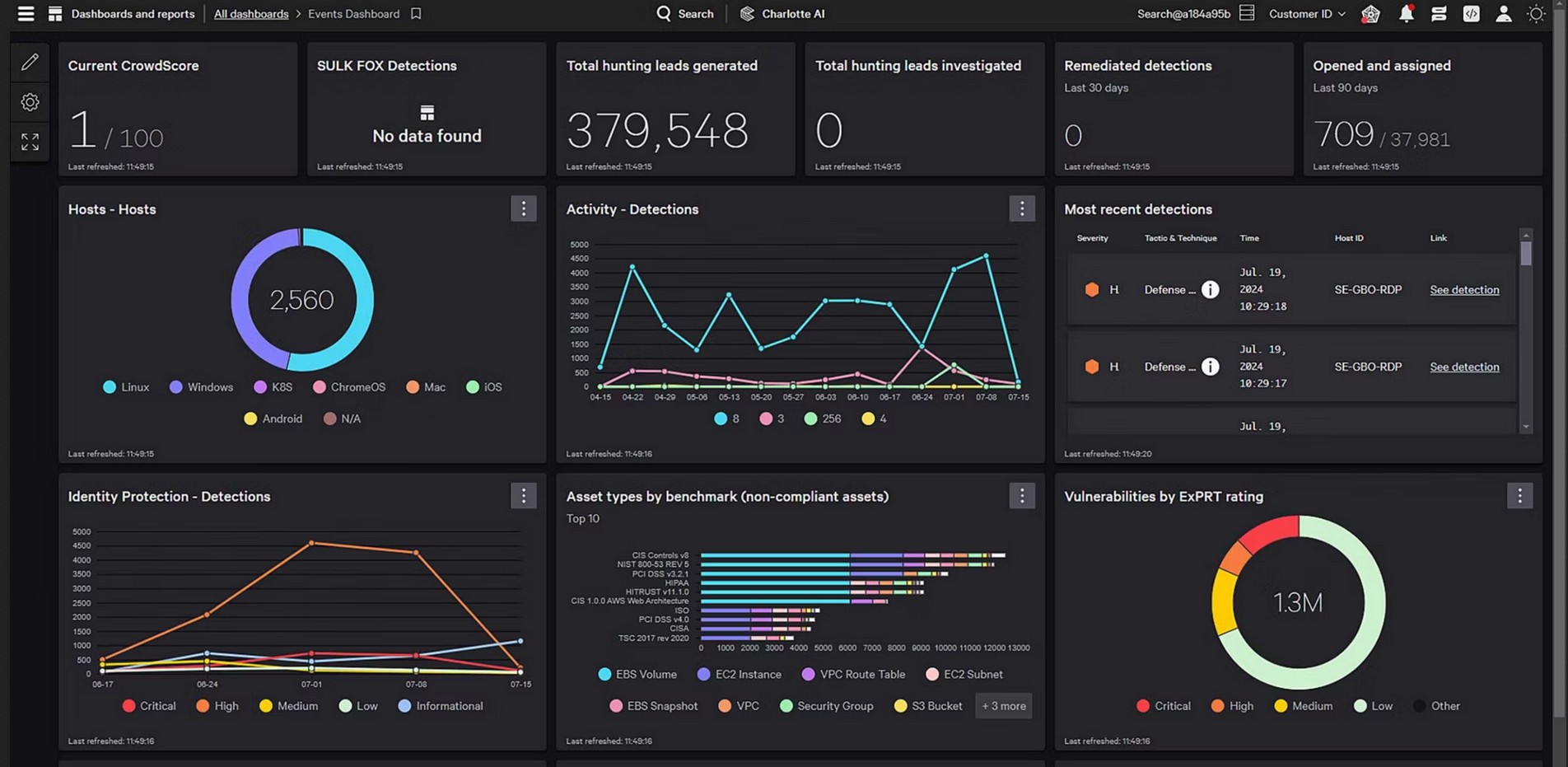
CrowdStrike is an advanced penetration testing service that tests the different components of your IT infrastructure to identify potential vulnerabilities. It also provides deep insights into your environment’s security posture and the possibility for attackers to exploit your vulnerability.
Source: CrowdStrike
Let’s now look at CrowdStrike’s PTaaS features.
Identifies Lateral Movement
CrowdStrike can assess how a hacker who enters your system can move laterally across your infrastructure. It can identify the speed and depth of the movement to give you an idea of the potential damage. Using a combination of strategies like exploitation and privilege escalation, CrowdStrike can assess lateral movements.
Assesses External Threats
Internet-facing systems risk the exposure of data to the outside world. To counter this exposure and to reduce unauthorized access to your sensitive data, CrowdStrike carries out tests for identifying potential vulnerabilities. These testing mechanisms include vulnerability discovery, exploitation, and enumeration.
Tests Web and Mobile Applications
CrowdStrike extensively tests your web and mobile applications to uncover vulnerabilities that lead to the loss of your sensitive data. It also checks for the possibility of compromise to your systems and data using a three-phase process of reconnaissance, discovery, and exploitation.
With these features, CrowdStrike is best positioned to identify threats to your systems and infrastructure and provides the contextual information required to mitigate them.
Pros:
- High levels of vulnerability detection.
- Excellent customer support and follow-up.
- Real-time testing.
- Protection against malware.
Cons:
- Limited reporting.
- Steep learning curve.
3. Intruder
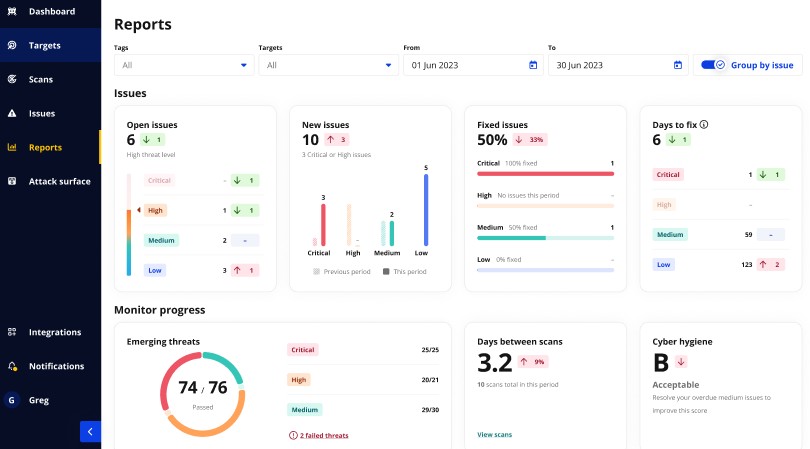
Intruder is an automated penetration testing tool that seamlessly connects with your existing digital infrastructure to test your systems and applications from a security standpoint. It also checks your systems for emerging vulnerabilities and helps mitigate them.
Source: Intruder
Below are the key features of Intruder PTaaS.
Automated Security Checks
Intruder uses automated security checks to identify vulnerabilities within your system. It is versatile and can support the scanning of your infrastructure, web apps, or APIs. These settings can even be configured to meet your organization’s specific needs. At the heart of these checks is a proprietary noise reduction algorithm that divides information from actionable insights, so you can focus on what matters the most. This information even helps with resource planning to address these security problems.
Continuous Monitoring
Intruder PTaaS continuously monitors your systems for multiple vulnerabilities like SQL injection, cross-site scripting, remote cloud execution flaws, weak encryption, security misconfigurations, and more. It can check around 140,000 types of attacks continuously. Moreover, the tool is easy to set up and you can get up and running with its monitoring within a few minutes.
Insightful Reporting
Many users find it hard to interpret the results of PTaaS scans because they are technical and complex. As a result, the impact of these tests gets lost. To avoid such a scenario, Intruder provides the context for each issue. Moreover, it uses simple language to explain the problem, ensuring that more people can understand the problem and its impact.
With such wide-arching features, Intruder PTaaS can help you make sense of vulnerabilities and address them before they are exploited by hackers.
Pros:
- Uses auto-scanning to detect vulnerabilities.
- Detects new vulnerabilities.
- Coordinates responses.
- Improves your security profile.
Cons:
- False positives can be lower.
- Unauthenticated website scans take a longer time to complete.
4. Astra Pentest
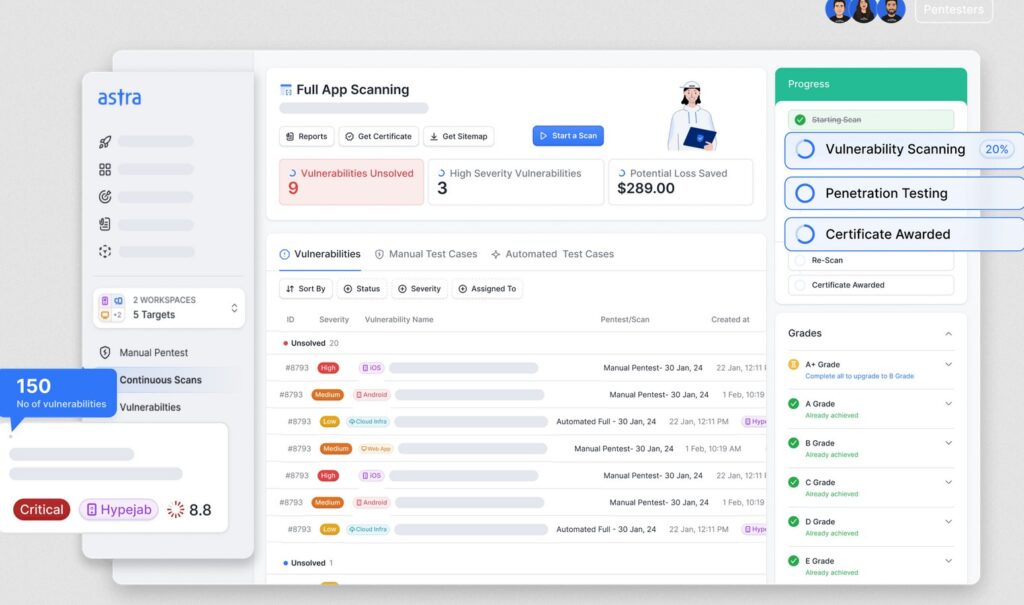
Astra Pentest is an advanced solution that comes with many next-gen features like an automated vulnerability scanner, in-depth manual testing options, and the ability to emulate the behavior of a hacker. Moreover, its unified dashboard provides all the information you need in a single place.
Source: Astra Pentest
Here are the important Astra Pentest features.
Vulnerability Scanner
The vulnerability scanner of Astra Pentest can scan all your assets comprehensively. Its 8,000+ automated scans can cover every possible cyberattack scenario documented in OWASP Top 10, SANS 25, and more. The advantage of this platform is that it uses regression tests and scans to continuously check your network for these vulnerabilities and report them.
Webpages Scanner
Astra can analyze the web pages behind login screens to check for any vulnerabilities in your web application. It even offers a browser extension that can effectively record logins and assess for any security gaps in the process. Also, it uses creative hacker knowledge to build on top of earlier pentest data and results to make the findings more insightful.
Well-designed Dashboards
Astra Pentest’s dashboards are well-designed to provide in-depth visibility into the results of your pentest. Moreover, it generates insightful data on the key metrics associated with each vulnerability to help you understand the root cause and allocate resources accordingly.
In all, Astra Pentest comes with many features to identify security loopholes in your system and fix them.
Pros:
- Excellent customer support.
- User-friendly interface.
- Extensive dashboards and reports.
- In-depth and automated scans.
Cons:
- Expensive, especially for small organizations.
- False positives.
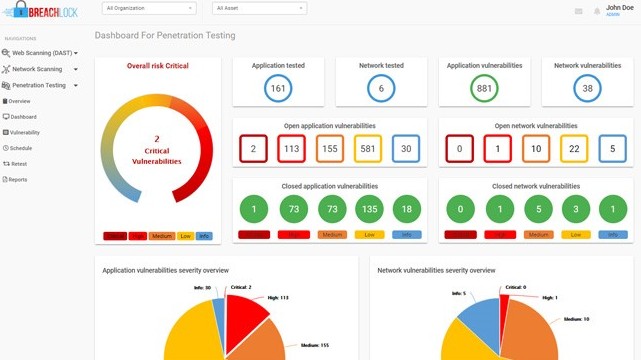
5. BreachLock
BreachLock is a continuous attack surface discovery and penetration testing platform that evaluates your platform to discover and mitigate potential vulnerabilities. It prioritizes exposures and backs them with evidence to help you allocate resources for fixing them.
Source: BreachLock
Below are the important BreachLock features that help with pen testing.
Applications Testing
BreachLock works well with your internal, external, mobile, web, and thick client applications. It analyzes the architecture and technology used to identify and validate vulnerabilities for their quick remediation. BreachLock specifically looks for weak authentication mechanisms, unauthorized access controls, business logic flaws, API security, and more. When it comes to external applications, it checks for vulnerabilities like injection attacks, cross-site scripting, data exposure, and more.
API Vulnerabilities
You can use BreachLock’s features to identify common API vulnerabilities like insecure data transmission, broken function level authorization, and more. You can use thorough input validation strategies and robust authorization mechanisms to improve the overall coding practices and API security.
Network Pentesting
BreachLock extensively tests your networks to identify and prioritize security weaknesses in your network. It also strengthens network security controls and improves the overall posture of your network. Furthermore, it simulates real-world attacks to evaluate the preparedness of your organization to handle and mitigate these attacks. It also supports host-based penetration testing and thick client testing to identify vulnerabilities in files and databases.
With such advanced features, BreachLock can identify many known vulnerabilities and can improve the outcome of your pen testing efforts.
Pros:
- Good customer support.
- Reliable and quick.
- Straightforward to use.
- Comprehensive and covers all aspects.
Cons:
- Reports can have better formatting.
- No on-demand scans.
Thus, these are the five best PTaaS tools to choose from. While most of them have the common functionalities of report generation and vulnerability scanning, some tools may be better suited for testing specific applications or scenarios unique to your organization. Consider your organization’s needs and the IT infrastructure setup to decide on the right fit.
Bottom Line
Penetration testing is a popular cybersecurity strategy where an ethical hacker and expert pen tester evaluates an organization’s security from a cyberattacker’s viewpoint. This pen tester will try the practices that an attacker will use to enter into a system and move through it. Based on the findings, the tester will generate a report detailing the organization’s vulnerabilities.
Given the complexity of this process, testers rely on pen-testing tools to carry out certain attacks. These tools can be on-premises or cloud-based. In this article, we evaluated the five best tools that offer pen testing as a service. We hope this information helps you identify the pen testing platform that works best for your organization.