Sensitive data is the confidential information that organizations collect, store, and process. It includes Personally Identifiable Information (PII) of customers and employees, credit card and other financial details, healthcare records if applicable, intellectual properties and assets, and anything else that can have serious consequences if it falls into the wrong hands.
In particular, governments worldwide heavily regulate the PII, necessitating organizations to take additional steps to safeguard them. Failure to adhere to these regulations can result in heavy fines and even a possible loss of reputation.
Here’s a look at the best software for discovering your sensitive data:
- iDox.ai An AI-powered compliance solution that provides valuable insights about your sensitive data and mitigates the risks associated with its storage and handling.
- Safetica A DLP and insider risk management solution that detects sensitive data and prevents breaches. It also protects against insider threats.
- Spirion An automated and continuous data discovery platform that can classify and remediate at-risk sensitive data.
- Mage A patented sensitive data discovery tool that can identify data across all data stores and locations. It works well on structured, unstructured, big data, and cloud data.
- ManageEngine DataSecurity Plus A data visibility and security tool that prevents insider threats and data loss due to human errors.
- Cohesity A data classification solution that uses ML-based scanning to discover and classify sensitive data.
- Datadog Sensitive Data Scanner A stream-based service that identifies, tags, and even redacts and hashes sensitive data for comprehensive protection.
- Varonis A data classification tool that can discover, classify, and lockdown sensitive and regulated data.
- Thales CipherTrust A unified data protection tool to discover, control, and protect your organization’s sensitive data.
- OneTrust Data Discovery & Classification A comprehensive platform that automates data discovery and classification to help make informed business decisions.
Organizations opt for a wide range of cybersecurity strategies to protect this sensitive information. However, the first step is to discover sensitive data across different mediums and locations to extend the organization’s security policies and cybersecurity strategies to them. This is where sensitive data discovery software comes in.
What is Sensitive Data Discovery Software?
As the name suggests, tools that identify sensitive data to protect it are called sensitive data discovery software. In today’s data-driven environment, sensitive data can be present in any format, ranging from images to documents. It’s not possible to manually stay on top of each piece of data that comes into your organization. This is why sensitive data discovery software is essential to automatically discover sensitive data based on semantics and patterns.
Read on to learn the best sensitive data discovery software tools, their features, pros, and cons.
Our Methodology
How did we pick these ten tools over the hundreds of others? Here are the evaluation criteria we used:
- Ability to search across multiple sites and file formats.
- Regular scanning of all data to identify any sensitive information.
- Support for GDPR, HIPAA, and other data security regulations.
- Integration with existing tech stack and data security systems.
- Robust report generation.
Best Sensitive Data Discovery Software
With this context, let’s jump into the tools and their capabilities.
1. iDox.ai
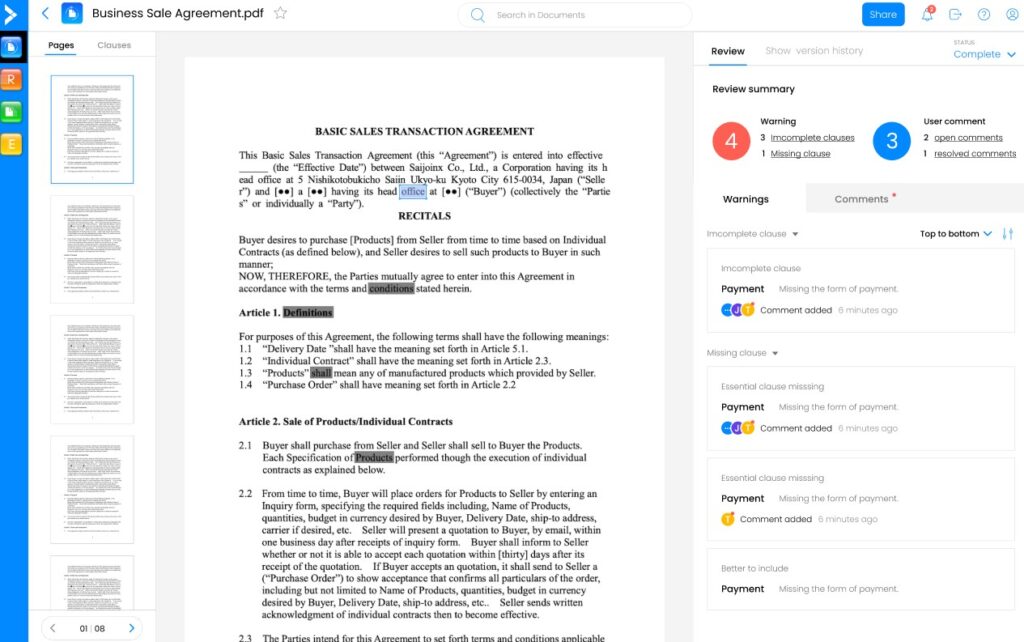
iDox.ai is an AI-based solution that can identify sensitive data and uncover insights about its storage, access, and handling. With this tool, you can not only reduce the risks associated with handling sensitive data but can also make the most of its potential while complying with regulations.
Source: iDox.ai
Here’s a look at iDox.ai’s sensitive data handling features.
Data Security
iDox.ai’s advanced data discovery tools detect and classify sensitive information across all data stores and storage devices. It can even detect trade secrets and proprietary information and protect them from unauthorized access. Moreover, these features can even meet the security requirements of cyber insurance providers.
Compliance
iDox.ai comes with robust compliance frameworks to safeguard PII. It uses AI to precisely identify data and ensure they meet regulatory compliance standards like GDPR and HIPAA. Besides, it also meets security and reporting regulations like SOX, SOC 2, PCI DSS, and more.
Integration and Customization
A highlight of this tool is that it integrates seamlessly with all tech stacks. Its APIs and extensions help you leverage iDox.ai’s capabilities without disrupting your existing workflows. Moreover, it is highly customizable and can align with your business and regulatory goals.
Overall, iDox.ai is a robust tool for sensitive data discovery, redaction, and protection.
Pros:
- Comprehensive compliance.
- Redaction features.
- Flexible deployment options.
- It has ISO 27001 and SOC 2 certifications.
Cons:
- No 24/7 support.
- Limited documentation.
Contact the sales team for pricing.
2. Safetica
Safetica is a data discovery and protection tool that can provide seamless protection for your PII, company’s IP assets, financial data, and other critical data assets you store and process. Its capabilities are well-suited for all organizations across different industries.
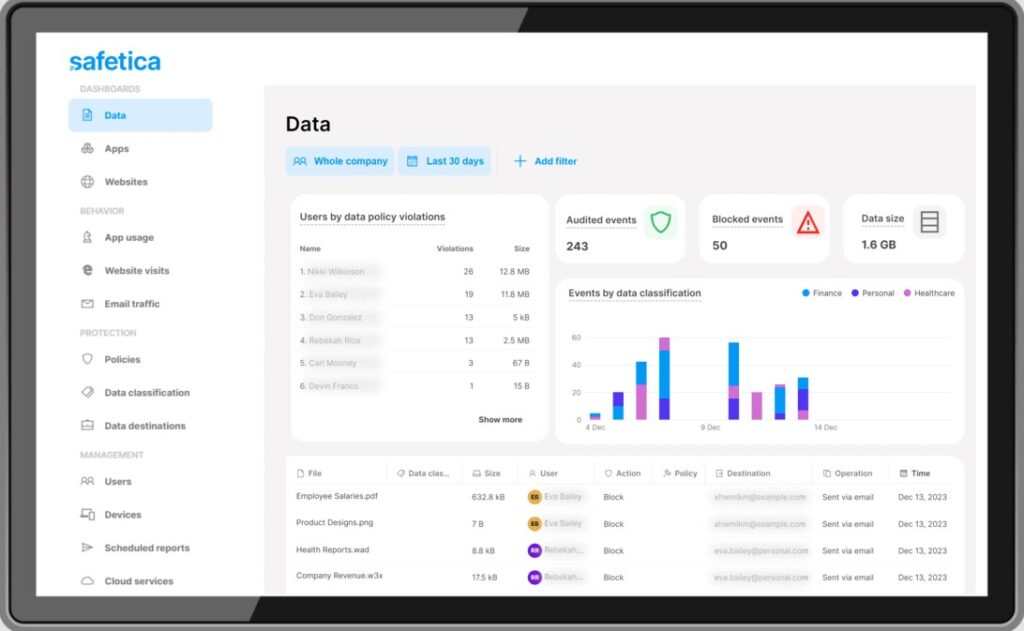
Source: Safetica
Below are Safetica’s important features.
Regulatory Compliance
Safetica uses advanced data security controls that meet your regulatory obligations. It provides complete visibility into how sensitive data storage is, who uses it and how, and so much more. Such information can help you comply with some of the most stringent regulations like GDPR, HIPAA, PCI-DSS, etc.
Intuitive User Interface
The user interface acts as a one-stop place to provide all the required information. It is intuitive and well-designed and makes it easy to effortlessly navigate through the different sections to find what you need. Also, no extensive training is needed to use this console.
Flexible Deployment
You can deploy Safetica on-premises or in the cloud to gain maximum security and control that aligns with your organizational needs. Moreover, you can use its policy templates to right away start detecting and logging incidents involving sensitive data.
In all, Safetica is a handy tool for protecting your sensitive data while complying with security and privacy standards.
Pros:
- It comes with data loss prevention capabilities.
- Robust encryption and authentication protocols.
- Good reporting and analytics.
- Meets compliance requirements for most industries.
Cons:
- The initial setup is challenging.
- It can be expensive for startups.
3. Spirion
Spirion is a data discovery and privacy solution that discovers personal, sensitive, and regulated data, regardless of where they are stored. This automated solution’s classification and protection mechanism safeguards your data and through it, ensures compliance.
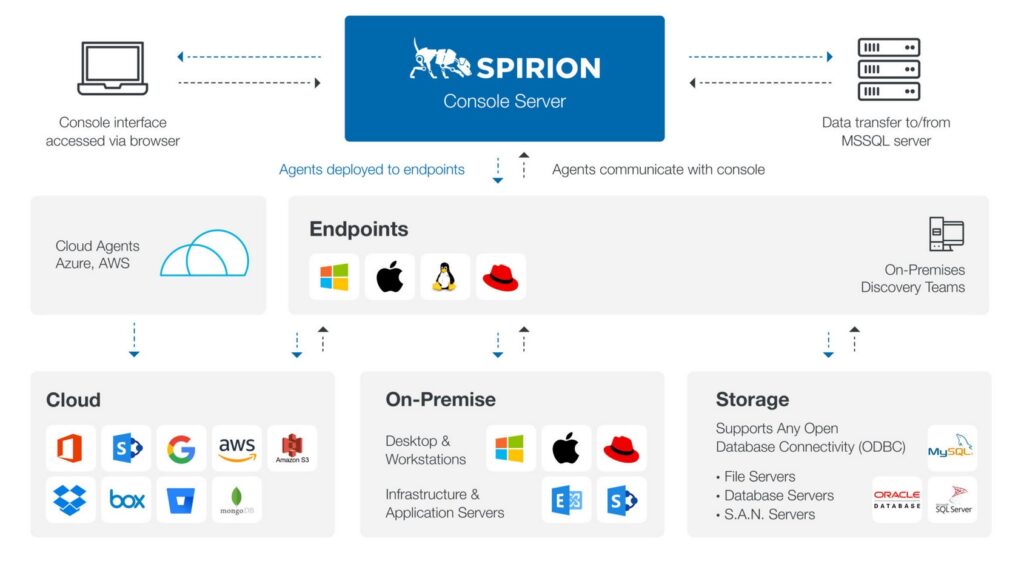
Source: Spirion
Let’s see how Spirion’s capabilities protect your sensitive data.
Extensive Coverage
Spirion integrates with a wide range of platforms to protect both structured and unstructured data. Some platforms it integrates with include Active Directory, Snowflake, Azure, Apple, Google Workspace, Microsoft Exchange, Oracle, Adobe, Red Hat Linux, and more.
Data Discovery and Classification
The first step in protecting sensitive data is to discover where it’s located. Spirion’s advanced features analyze every area in your organization to identify sensitive data based on semantics. Next, it classifies this data with a wide range of dynamic and persistent labels, tags, and visual markers for easy identification.
Continuous Monitoring
Spirion’s Sensitive Data Watcher is a tool that continuously scans your sensitive data to provide real-time insights about data usage and access. It also provides active threat detection and comprehensive control and visibility.
With such features, Spirion can go a long way in safeguarding your sensitive data, thereby helping you meet the compliance requirements as well.
Pros:
- Streamlined GUI.
- Ensures that your organization’s security policies are followed.
- Helps compliance with industry standards.
- Prevents data loss.
Cons:
- Steep learning curve.
- The interface can be more user-friendly.
4. Mage Data
Mage can uncover sensitive data located across all locations in your organization, regardless of the underlying data type. It works well with unstructured and big data as well. The advantage of using this tool is that you can identify the hidden risks associated with sensitive data and fix them to ensure security and privacy.
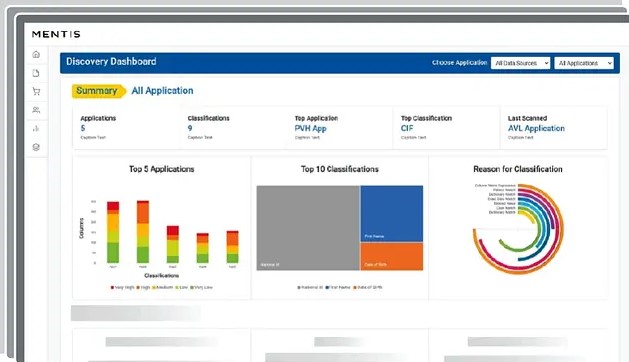
Source: Mage
Below is Mage’s sensitive data handling capabilities.
Data Security Risks
Mage uses AI, machine learning algorithms, and Natural Language Processing (NLP) to locate sensitive data spread across the most obscure and complex locations. Its patented technology minimizes false positives and improves the efficiency rate of identification.
Out-of-the-box Templates
This platform comes with 80+ out-of-the-box templates to identify commonly used sensitive data like Personal Health Information (PHI), PII, IP assets, and more. You can even customize these templates to identify the data types that are unique to your organization.
Data Regulation and Compliance
The last few years have seen the emergence of many privacy regulations that are continuously evolving to meet the growing data volumes. Mage is scalable and future-proof and can adapt well to these changing regulations to ensure 100% compliance always.
In all, Mage sets the stage for streamlined data protection by identifying sensitive data across different locations.
Pros:
- Intuitive and data-rich dashboards.
- Scalable and flexible.
- Distributed architecture to identify sensitive data across multiple locations.
- Compatible with many data repository platforms.
Cons:
- Customer service can be better.
- Limited filtering options.
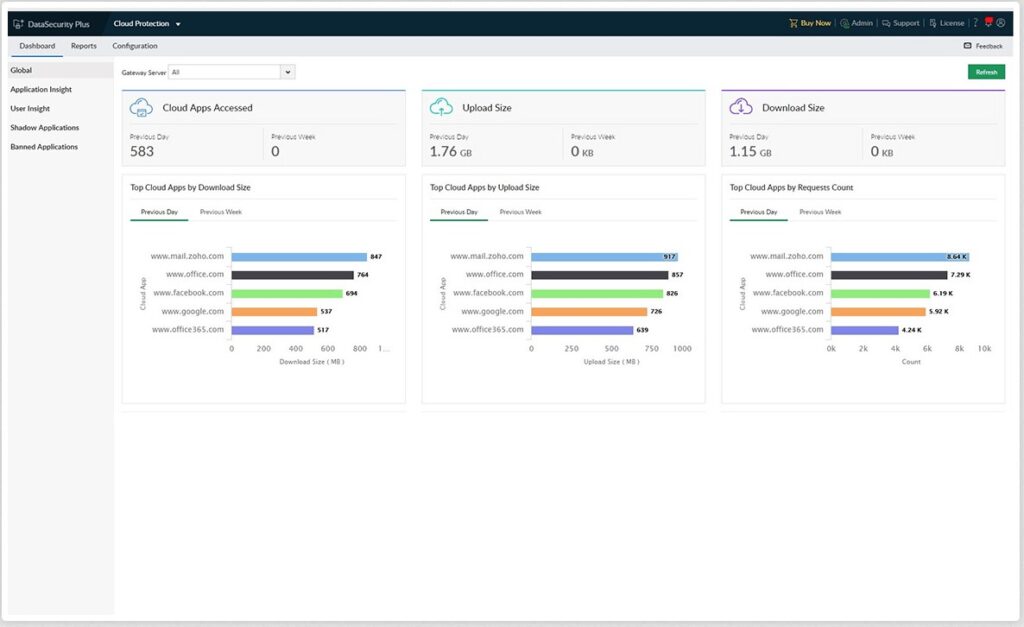
5. ManageEngine DataSecurity Plus
A part of Log360, ManageEngine DataSecurity Plus fights insider threats and prevents data loss due to human errors while ensuring regulatory compliance with leading standards. It also safeguards data against data thefts, ransomware, and other cyber threats.
Source: ManageEngine
Let’s look at the data discovery features of this tool.
File Integrity
Files may contain sensitive data and this is why DataSecurity Plus spots unusual file activities and unauthorized file transfers to ensure that the sensitive data is not compromised in any way. Moreover, you can configure this tool to block file copy actions across your entire network.
Prevents Insider Threats
DataSecurity Plus continuously monitors all file activities, removable device usage, data transfer rates, and application use to detect potential insider threats. Based on its findings, the tool notifies administrators to proactively prevent these attacks.
Web Security
With this tool, you can scrutinize the use of shadow IT apps and services to prevent them from leaking sensitive data. Also, it can analyze the impact of productivity-draining applications like social networking. Moreover, it can detect potential security threats like ransomware and data exfiltration attempts and even automate responses.
In all, DataSecurity Plus is a comprehensive tool to protect your sensitive data from cyber-attacks and unauthorized access.
Pros:
- Tracks file modifications for integrity and security.
- Improves compliance with PCI, SOX, FISMA, and more.
- Generates meaningful audit reports in real time.
- Checks for the presence of clear text PII within all file types.
Cons:
- The user interface can be better.
- The risk analysis setup is complex.
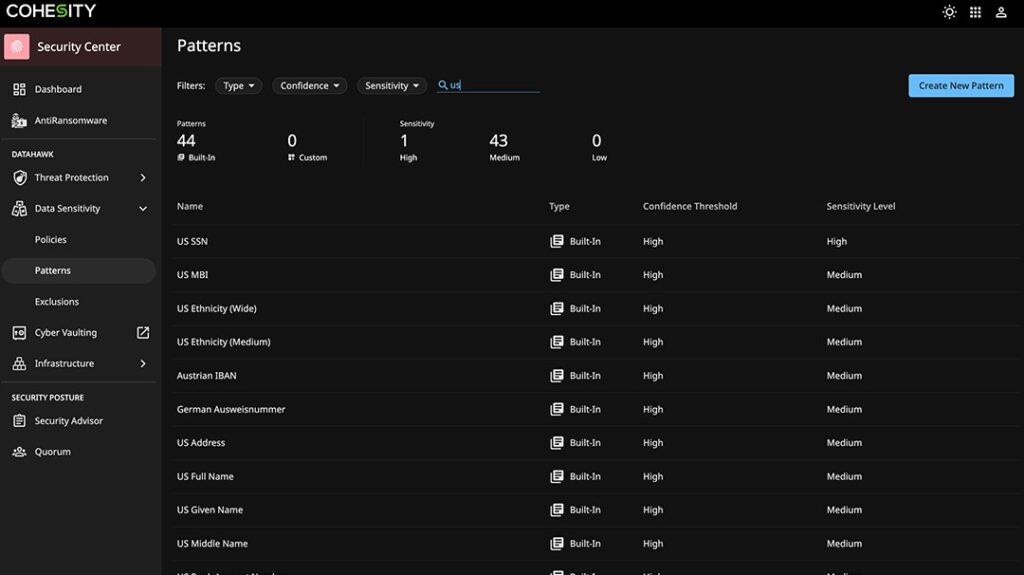
6. Cohesity
Cohesity is a data discovery platform that uses machine learning and an NLP-based classification engine to accurately identify sensitive data across different locations and formats. More importantly, it helps you assess ransomware attacks and protect your data.
Source: Cohesity
Here’s a look at Cohesity’s sensitive data discovery features.
Built-in Templates and Patterns
Cohesity comes with more than 235 built-in patterns to identify all kinds of sensitive data across different formats. You can even customize these templates or combine them with custom policies to automate the discovery of sensitive data. This streamlined approach helps with regulatory compliance as well.
Minimal False Positives
This tool uses machine learning and NLP to identify false positives in notifications, so you can focus on provisioning resources to identify and mitigate threats to your sensitive data. It also uses regex matching to filter results and provide the most relevant ones.
Intelligent Masking
Cohesity uses intelligent masking capabilities to scrub and redact documents that contain sensitive data. With this approach, your PII and other information remain protected even if the document is breached.
In all, Cohesity is a data discovery tool that returns accurate results because of ML algorithms.
Pros:
- Unified platform for managing your sensitive data.
- Extensible APIs.
- ML-powered cybersecurity.
- Easy-to-use GUI
Cons:
- Customer support can be better.
- Limited log and error reporting.
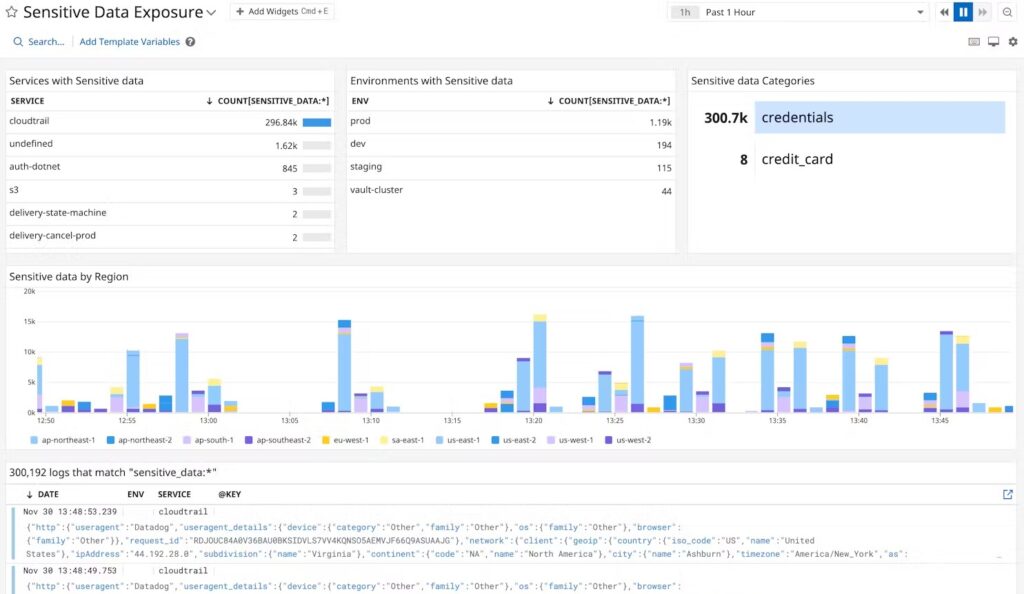
7. Datadog Sensitive Data Scanner
Datadog’s Sensitive Data Scanner helps build a modern compliance framework as it automatically identifies sensitive data and redacts or hashes them from public view. It can do these operations at scale and in real-time to help your organization meet the requirements of GDPR, HIPAA, and more.
Source: Datadog
Below are the important features of Datadog Sensitive Data Scanner.
Configurable Scanner
A highlight of this tool is the granular control and flexibility it offers over what is sensitive data. With this tool, you can define what data you want to scan, the filters you want to use, and the modules you want to enable for scanning like Log Management, RUM, etc. The advantage of this control is that you can adapt the tool to meet any compliance requirement by simply tweaking its configurations.
Sensitive Data Classification
With Datadog, you can standardize the classification of sensitive data across the dev, operations, and security teams across cloud and hybrid environments. You can also set up and customize out-of-the-box rules to capture common patterns. Moreover, you can formulate policies that match your process.
Redact Data
Datadog can redact or scrub all the sensitive data located across documents and other file formats, helping you meet compliance requirements. Also, you can leverage its audit logs and role-based access controls to build a comprehensive compliance strategy.
Overall, Datadog Sensitive Data Scanner is an advanced tool that identifies and handles your sensitive data.
Pros:
- Integrates well with other products.
- Supports real-time log monitoring.
- Streamlined notifications.
- Built-in dashboards
Cons:
- Complex setup.
- Customer support can improve.
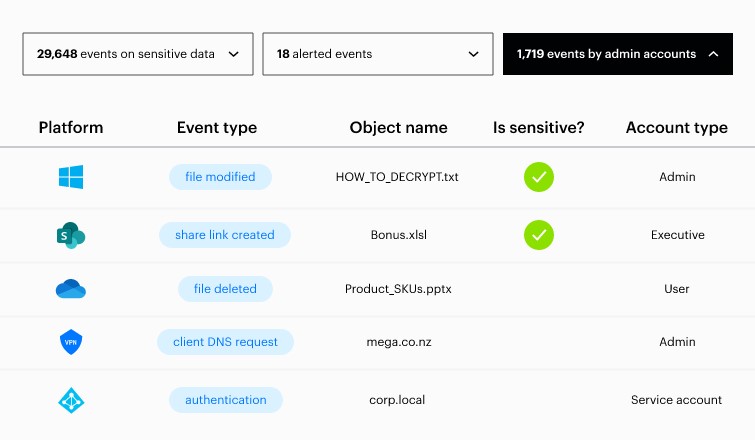
8. Varonis
Varonis is a data classification engine that automatically classifies sensitive data, reduces their exposure, and generates alerts on suspicious access and behavior. It also generates reports and helps compliance with regulatory laws.
Source: Varonis
Read on to understand how Varonis can classify and protect your sensitive data.
Extensive Automation
One of the standout aspects of Varonis is its automation across different operational areas. You can automatically apply labels to sensitive data, revoke unnecessary access, and index regulated data to quickly handle DSAR requests. Such automation saves time and effort while meeting compliance with regulations like GDPR.
Policy Enforcement
With Varonis, you can auto-enforce your data governance policies within minutes. You can also customize this automation to fit into your organization’s policies to move or archive sensitive data. The advantage is that you can build rules with out-of-the-box filters, flags, tags, or labels.
Data Risk Visualization
Varonis provides comprehensive views of data risks across your cloud and on-premises storage. With this view, you can better understand the concentration of sensitive data and can accordingly, frame organizational policies to protect them.
Overall, the automation features of Varonis can ease your time and effort in protecting sensitive data.
Pros:
- Extensive and precise automation.
- Robust logging.
- Integrates well with Active Directory.
- Customizable dashboard.
Cons:
- Expensive
- It requires more resources.
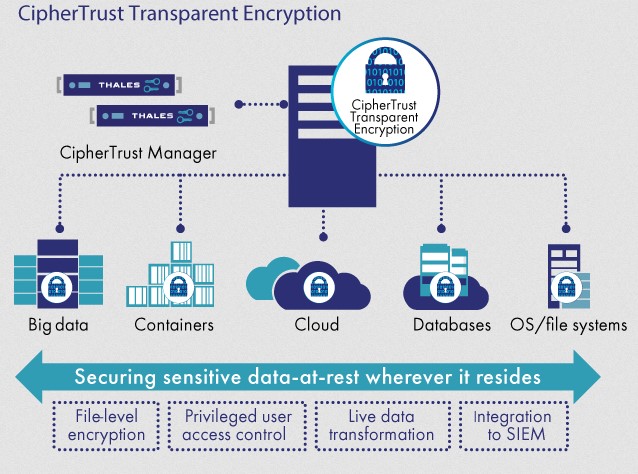
9. Thales CipherTrust
CipherTrust is a data security platform that discovers and protects your organization’s sensitive data located anywhere. Built on modern microservices architecture, this tool brings together all the processes, from discovery to remediation.
Source: Thales
Complete Visibility
CipherTrust offers complete visibility into your sensitive data stored on the cloud and on-premises. Moreover, its data discovery capabilities identify sensitive data located in files, big data, databases, and anywhere else in your infrastructure.
Secure Protection
Thales CipherTrust offers multiple mechanisms to protect your data like encryption and tokenization. With this strategy, the organization is responsible for storing and maintaining the encryption keys, thereby providing complete control over data privacy. Moreover, it offers capabilities like file-level encryption, application-layer encryption, static data masking, vaultless tokenization, and more.
Simple Administration
CipherTrust has eliminated complexity from the everyday management and administration of sensitive data. It uses a single platform to manage all the encryption keys. Also, you can control granular access and monitor usage through this dashboard, making it ideal for people of all technical backgrounds.
Due to these features, CipherTrust streamlines the discovery and protection of your sensitive data.
Pros:
- Well-developed user interface.
- Extensive data protection
- Ensures compliance.
- Protects Kubernetes data space.
Cons:
- Limited third-party integrations.
- Limited documentation.
10. OneTrust Data Discovery & Classification
OneTrust provides visibility into your sensitive data, including its location and who has access to it. More importantly, it automatically inventories and classifies data to ensure that it is used responsibly and safely throughout its lifecycle.
Source: OneTrust
Let’s now look at OneTrust’s data discovery features.
AI Capabilities
OneTrust uses AI to discover and classify sensitive data. It scours through structured, unstructured, and semi-structured data spread across files, cloud, big data, and databases to identify sensitive data. It can work across any data format to identify the data that requires protection.
Security Controls
This platform uses a combination of techniques to identify the at-risk data and accordingly, enforces security controls. Moreover, it continuously analyzes the security to identify deviations and notifies the concerned users for immediate action.
Enhanced Privacy
OneTrust uses privacy by design which means no one can copy sensitive data or transfer it outside the organization. Also, it will not be used to train AI models outside of the organization’s environment.
Overall, these features make OneTrust a reliable data discovery and classification tool to manage your sensitive data.
Pros:
- Helps service data requests.
- User-friendly interface.
- Saves time and effort.
- Highly customizable.
Cons:
- It has a learning curve.
- Customer support can improve.
Thus, these are the ten best tools for discovering, classifying, monitoring, and protecting your sensitive data.
Bottom Line
Managing sensitive data can be complex and error-prone if you don’t have a streamlined process to discover and classify them. Without proper classification, the sensitive data can get exposed to unauthorized users, resulting in financial loss. Moreover, failure to meet standards like GDPR can also result in heavy fines and penalties.
The first step to avoid these security consequences is to identify and classify sensitive data, so you can enforce appropriate policies. The tools mentioned in this guide can handle this classification for you. We hope this information helps you to better protect your at-risk data.