The AICPA (American Institute of Certified Public Accountants) developed a framework of security controls known as SOC. It is a voluntary security and compliance standard designed for service organizations. SOC 2 revolves around how organizations handle sensitive customer data and protect it from unauthorized access, cyberattacks, and other security vulnerabilities. The idea behind complying with SOC 2 is to instill confidence in the minds of customers, investors, and other stakeholders about the security and integrity of their data.
Below are the best SOC 2 compliance software and tools:
- Mitratech Alyne A comprehensive Governance, Risk, and Compliance (GRC) platform that automates many processes to reduce the manual time and effort involved. Also, it provides the controls, assessments, and reports required for compliance.
- Vanta A SOC 2 automation software that offers continuous testing for SOC 2 compliance. It also gathers evidence for security audits.
- Netwrix A governance platform that supports both on-premises and hybrid cloud environments. It also offers complete control over changes and configurations across all environments.
- Protecht Group A risk management software that provides the insights you need to protect your sensitive data, enabling SOC 2 compliance.
- Drata An automated platform for managing risks and complying with SOC 2 principles.
- Apptega A cybersecurity compliance software that eases SOC 2 compliance processes and efforts.
- Hyperproof A compliance platform that continuously evaluates risks and actions to help organizations gain SOC 2 compliance quickly and cost-effectively.
- AuditBoard A framework for managing compliance with SOC 2 and other regulations.
- Secureframe An advanced compliance software that condenses the 200+ controls related to SOC 2 compliance into eight easy steps.
- Scrut An information security program that oversees various aspects related to SOC 2 compliance and ensures they meet the stipulated guidelines.
SOC 2 is designed more as a security framework that encompasses the following five items:
- Security: Protecting data from unauthorized access.
- Availability: Ensuring that employees have a reliable and accessible system and data to complete their assigned responsibilities.
- Processing Integrity: Proof that an organization’s systems and processes work as they should.
- Confidentiality: Limiting the access and storage of confidential data.
- Privacy: Protecting the sensitive data of customers from unauthorized users.
The above five aspects are together called the Trust Service Criteria.
Moreover, there are two types of SOC 2 audits and these five criteria apply to both types.
SOC 2 Type I checks the company’s security controls at a specific time and broadly checks if the controls are designed to protect the sensitive data of customers. The SOC 2 Type II audit, on the other hand, checks the controls and their impact over a period, generally three to 12 months. It checks if the controls are effective in protecting customer data.
Out of the two types, the first is easier to achieve, while the second is more reliable and makes your operations trustworthy in the eyes of your stakeholders.
SOC 2 Audits
The audit process of SOC 2 is flexible because every organization’s needs are unique. This is why they have the option to create and implement internal controls that meet the above criteria. An independent auditor completes the audit to see if the organization’s internal controls support the Trust Service Criteria.
After evaluating the processes and controls against the five criteria mentioned above, the auditor will create a report and will provide one of the following results:
- Unqualified: The company’s systems and processes comply with the framework.
- Qualified: The company passed the audit but requires improvements in some areas.
- Adverse: The company failed the audit.
- Disclaimer of Opinion: The auditor does not have enough information to make a fair decision.
Though SOC 2 audits are not as stringent as HIPAA, they still require considerable effort and processes that are hard to manually implement, especially if your organization is large or spread across different global locations. This is where SOC 2 compliance software and tools come in handy.
Our Methodology
With many SOC 2 compliance tools, picking just 10 is not easy. Here are the criteria we used for evaluating each tool:
- Automatically collects evidence, bringing down the manual efforts required.
- Integrates with all tech stacks
- Ability to evaluate third-party vendor security.
- Support for custom controls that align with your organization’s operations.
- Availability of training modules for employees.
Best SOC 2 Compliance Software and Tools
With this context, let’s see the features of each tool in depth.
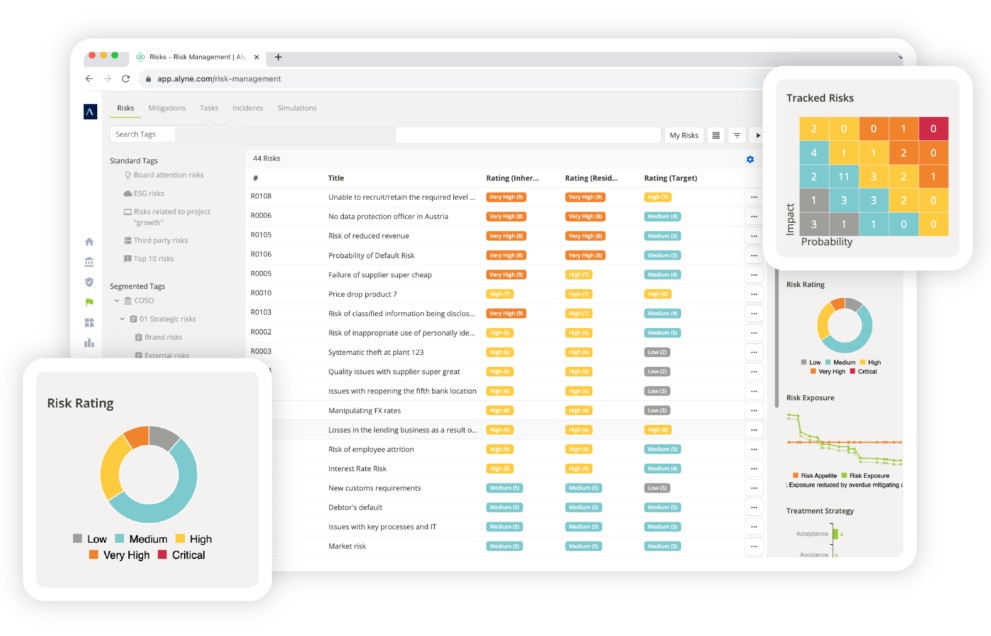
1. Mitratech Alyne
Mitratech Alyne is a comprehensive GRC platform that offers many out-of-the-box features to streamline controls and assessments. Moreover, its well-designed templates help with creating reports and understanding the gaps that exist in SOC 2 compliance.
Source: Mitratech
Below are the key Alyne features that help with SOC 2 compliance.
Control Set
Alyne offers 625 controls in its library of templates. These controls are highly structured, granular, and easily customizable to meet every organization’s specific requirements. Furthermore, you can set the scope of these controls to meet SOC 2 and other compliances as well.
Risk Reports
Risk reports help internal auditors understand the existing gaps, so they can formulate the strategies needed to mitigate them. Alyne can create risk reports geared specifically for SOC 2 compliance and identify the gaps to ease the efficiency of your auditors.
Leverages AI Technology
Alyne uses Artificial Intelligence (AI) and Machine Learning (ML) technologies to continuously learn and understand your requirements and provide tailored suggestions for SOC 2 compliance. Moreover, it continuously monitors updates and converts them to your organization’s specific needs.
With these features, Alyne can help you reach SOC 2 compliance, regardless of whether you are starting or closer to the end.
Pros:
- Easy to create custom assessments.
- Helps align controls with processes.
- Effective validations.
- Extensive evidence collection.
Cons:
- No on-premise deployment.
- Limited integrations.
EDITOR'S CHOICE
Mitratech Alyne is our top pick for SOC 2 compliance because it has all the features an organization needs to create custom controls and map them with their organization’s processes and goals. Its extensive reporting coupled with change monitoring make it a handy tool for all organizations looking to become SOC 2-compliant.
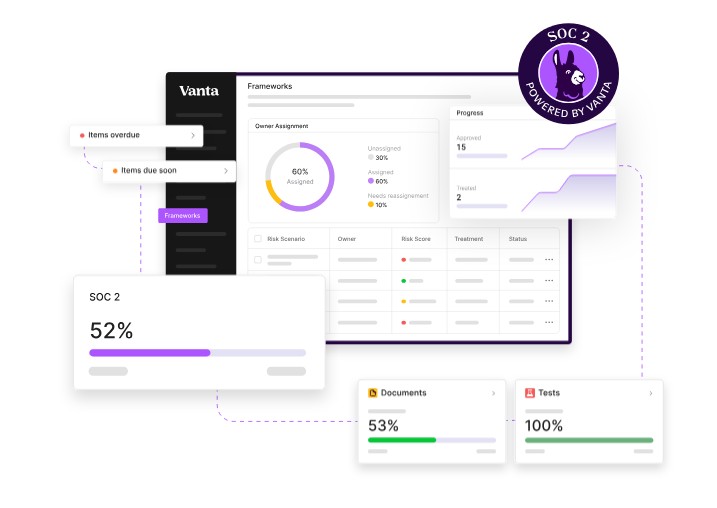
2. Vanta
Vanta is a powerful platform that supports all organizations through their SOC 2 compliance journey. It automates many compliance processes and provides a seamless audit experience. Moreover, Vanta has a set of vetted auditors who can also help with compliance.
Source: Vanta
Here’s a look at the important features that help with this compliance.
Evidence Gathering
One of the most complex tasks in any compliance program is to gather evidence, and Vanta eases this process for organizations. It automatically connects with third-party vendors like cloud operators, identity providers, and others to gather the evidence required for security audits.
Centralized Security
Another key feature of Vanta is the centralized security controls. With Vanta, you can onboard and offboard employees, remediate issues from failed tests, manage documents, and more through a single dashboard. As a result, you have comprehensive visibility into how sensitive information is handled within your organization.
Smart Templates
Vanta automatically pre-fills templates with the data you have entered, thereby saving you time and effort. Also, it supports using custom controls and mapping them to existing templates for SOC 2 compliance.
Overall, Vanta has many features that support compliance without spending many hours and resources.
Pros:
- Intuitive user interface.
- Excellent customer support.
- API capabilities for custom integrations.
- Well-designed templates
Cons:
- Steep learning curve.
- Better control in the Vanta app.
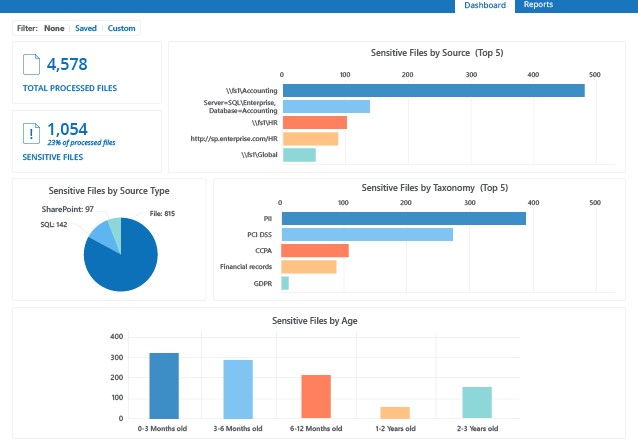
3. Netwrix Auditor
Netwrix Auditor is a governance platform that protects data across multiple environments. Its security analytics quickly detects anomalies in user behavior and provides actionable insights to fix them. At the same time, it provides visibility into critical systems for authorized users.
Source: Netwrix
Below are some Netwrix features that enable SOC 2 compliance.
Templates and Standards
Netwrix offers a good starting point to start on your compliance journey. Its out-of-the-box templates, best practice suggestions, and password policies help you set the framework for compliance.
Insights into Regulated Data
When you know the source of your regulated data, you can take concerted steps to ensure its safety. Netwrix offers information about the source and storage of your regulated data, so you can optimize its workflow and protect it from unauthorized access.
Strong Password Policies
Netwrix provides many out-of-the-box regulations and frameworks to improve the security of your passwords. Moreover, its templates help to enforce password policies, without causing frustration to users.
In all, Netwrix has many convenient features and templates to create a SOC 2 compliance environment.
Pros:
- Tracks Active Directory changes and modifications.
- Unified dashboard
- Integrates with many third-party platforms.
- Works well across multiple environments.
Cons:
- Configuration is complex.
- Better documentation.
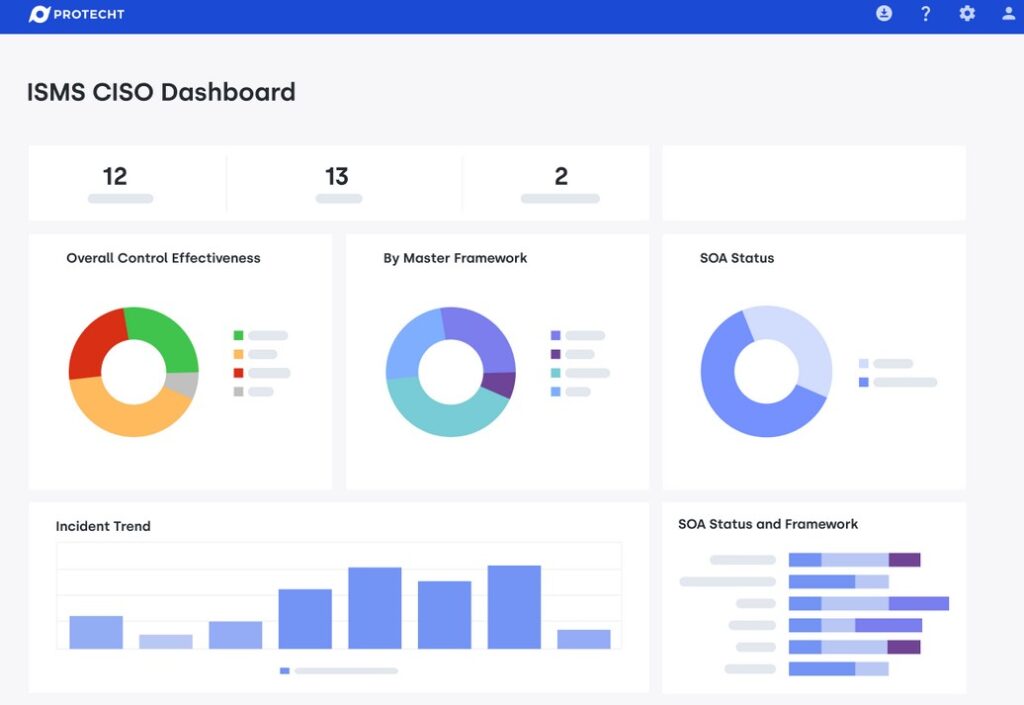
4. Protecht Group
Protecht Group offers a unified risk management solution that continuously evaluates your risks from different sources. It also provides insights into these risks and the actionable steps you can take to protect the sensitive data of your customers. With its many features, you can ensure compliance with SOC 2’s trust principles.
Source: Protecht Group
Here’s a look at Protecht’s features that ensure seamless SOC 2 compliance.
Centralized Risk Management
Protecht integrates IT and cybersecurity risks on a single platform to provide the comprehensive visibility you need over the likely risks. It also continuously assesses the policies to help you secure customer data from unauthorized access and other cybersecurity risks.
Reporting Library
Its reporting library houses many out-of-the-box templates that you can leverage to comply with SOC 2 regulations. These templates are based on industry best practices and can boost your overall security and control over sensitive data.
Incident Management
Protecht’s incident management capabilities help capture security breaches and incidents and analyze them for insights. Accordingly, it provides suggestions to respond and recover from these incidents.
In all, Protecht Group offers integrated risk management to demonstrate compliance with SOC 2 principles.
Pros:
- Clean and user-friendly interface.
- Structured dashboards and reports.
- Customizable forms and templates.
- Automated notifications.
Cons:
- Customer support can be better.
- A learning curve is involved.
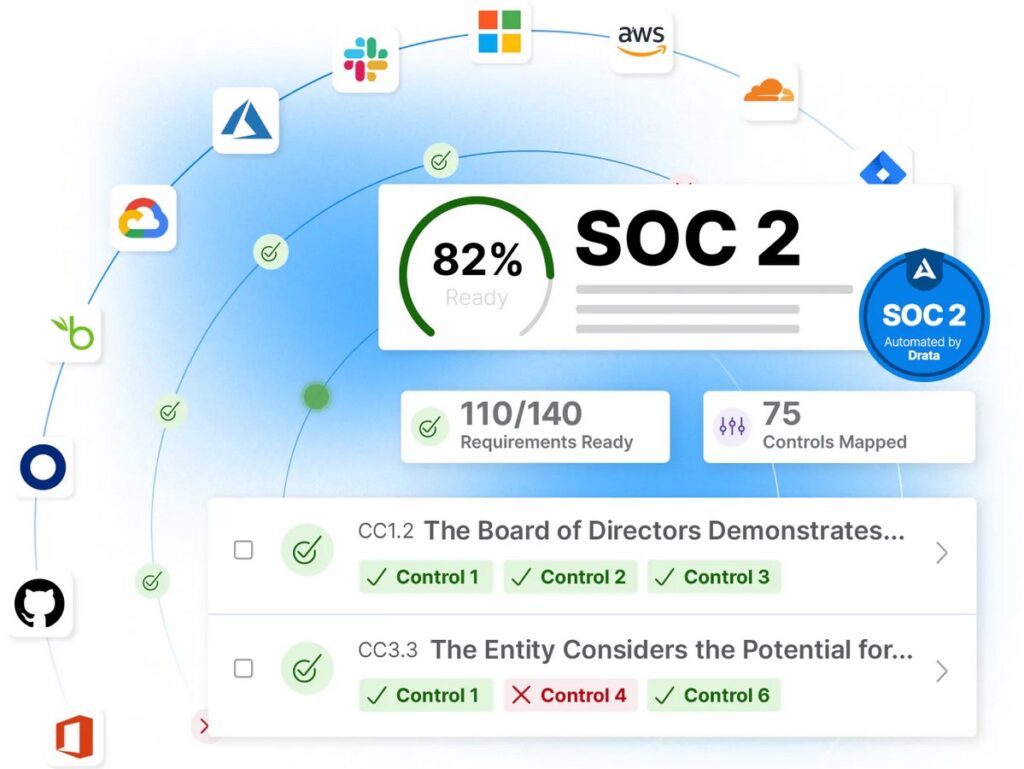
5. Drata
Drata is a streamlined platform that automates the SOC 2 processes to help you gain the trust of your customers and key stakeholders. Besides getting you up and running in minutes, it saves time and effort and reduces the likely errors that come with manual handling.
Source: Drata
Let’s now look at the Drata features that enable SOC 2 compliance.
Automates Evidence Collection
Drata automates the process of collecting evidence. It integrates with more than 120 applications natively and combines them with your tech stack to seamlessly collect evidence and analyze them for compliance gaps.
Reduces Compliance Costs
Its workflow automation capabilities streamline monitoring and tracking. It even provides a single source of truth to help you quickly respond to data requests. Moreover, these capabilities scale with your organization’s growth, thereby reducing compliance costs over time.
Compliance Experts
Drata partners with compliance experts and can connect you with the experts who can best handle your compliance and audits. Moreover, it provides a single source of truth that can come in handy for these audits.
Due to such advanced automation features, Drata can take you closer to SOC 2 compliance with minimal time and effort.
Pros:
- Extensive automation,
- Availability of expert support and guidance
- Centralized repository for all evidence.
- Preconfigured frameworks are handy for identifying compliance gaps.
Cons:
- The user interface can be confusing at times.
- Expensive.
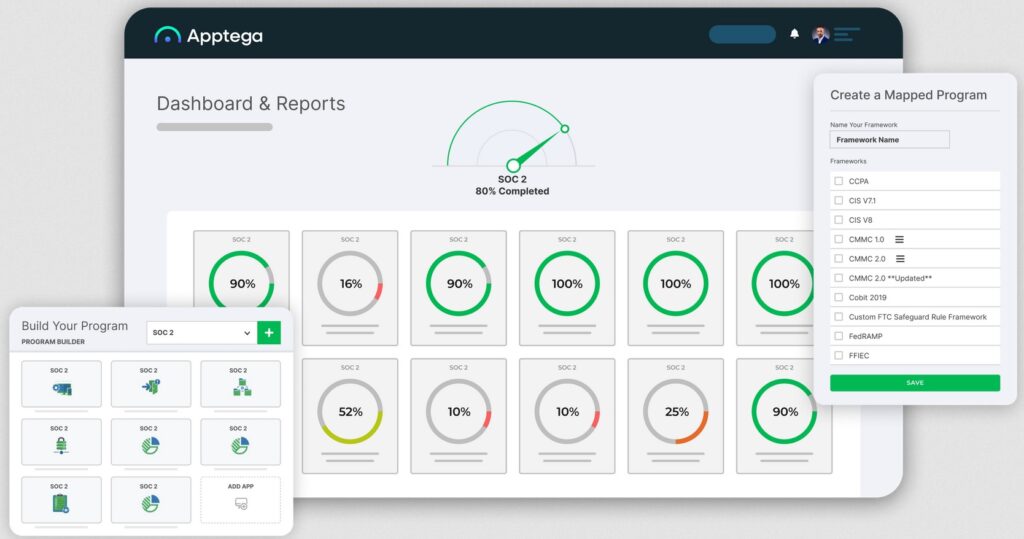
6. Apptega
Apptega is a cybersecurity compliance platform that offers compliance-as-a-service for organizations with limited resources. It presents a framework for a faster and stronger approach towards SOC 2 compliance.
Source: Apptega
Below are the key Apptega features that can help with SOC 2 compliance.
Automated Assessments
Apptega offers a simple questionnaire-styled assessment to collect evidence for every action as you perform it. Later, you can correlate this data and analyze them to better understand the gaps and remediate them.
Linking Evidence
With Apptega, you can quickly link evidence with your assessments because of the built-in mapping done while entering the data. During this mapping, you can also identify what’s missing and add them to strengthen your compliance levels.
Support Collaboration
You can easily share data with other stakeholders involved in the SOC 2 compliance process. You can also assign tasks to individual members and get updates from them as you move along the SOC 2 compliance process.
Overall, Apptega has all the features you need to earn smooth and hassle-free SOC 2 compliance.
Pros:
- Responsive customer support.
- Its risk-based approach makes it easy to identify gaps.
- Cross-framework mapping and evidence collection ease the compliance process.
- Scales well.
Cons:
- The user interface can be a bit clunky.
- Limited integrations.
7. Hyperproof
Hyperproof is a compliance software that helps companies comply with SOC 2 Type I and Type II audits. It comes with many features that speed up the compliance process while reducing the associated costs. Moreover, Hyperproof also partners with professional services companies to conduct readiness assessments and audits.
Source: Hyperproof
Let’s look at Hyperproof’s features that enable SOC 2 compliance.
Well-developed Templates
A standout feature of Hyperproof is its well-designed templates that translate the SOC 2 compliance criteria into actionable insights that are relevant to your organization. It helps break down the key milestones into small chunks, making it easier for you to allocate resources and meet the deadlines.
Evidence Gathering
Hyperproof gathers evidence of your SOC 2 compliance and shares it with the compliance teams and auditors for seamless collaboration. It also stores the evidence in a centralized place, so you can reuse them across multiple frameworks and controls.
Gauge Progress
Assigning responsibilities and gauging their progress can simplify SOC 2 compliance, and Hyperproof empowers you to do both. With this tool, you can easily assign specific tasks to individuals and teams and monitor their progress through the dashboards.
With such features, Hyperproof scales well with your operational growth while incurring compliance.
Pros:
- Excellent customer support.
- Continuous compliance.
- Highly customizable.
- No coding or complex configurations are required.
Cons:
- Limited SaaS integrations.
- Limited customization of dashboards and reports.
8. AuditBoard
AuditBoard brings together risks, controls, frameworks, and more to streamline SOC 2 compliance. Its ability to manage compliance issues and collaborate with stakeholders can further drive your compliance efforts.
Source: AuditBoard
Below are some key features that help with SOC 2 compliance.
Risk Assessments
With its standardized templates, AuditBoard streamlines risk assessments. It even ranks the severity of each risk and provides a score for each to help you prioritize and plan remediation.
Evidence Gathering
AuditBoard proactively schedules and sends requests to specific individuals to provide the information needed for compliance and stores them in a central location. Moreover, it also reduces fatigue by ensuring that the evidence you collect once can be reused across multiple scenarios.
Report Creation
AuditBoard centrally locates all data including audit trails and this process comes in handy for report generation. Furthermore, you can gain comprehensive visibility into open issues and gaps, remediate them, and track their progress.
In all, AuditBoard eases SOC 2 compliance with its centralized storage and templates.
Pros:
- Easy to manage audit-related processes and tasks.
- Supports collaboration.
- Centrally stores all data.
- Automates evidence gathering.
Cons:
- The user interface can be better.
- Limited customer support.
9. Secureframe
Secureframe is a compliance framework that eases the process of obtaining SOC 2 compliance. According to its website, you can get compliance within weeks when you use Secureframe because it streamlines every task involved.
Source: Secureframe
Here’s a look at SOC 2 compliance-related features of Secureframe.
Comprehensive Compliance
With Secureframe, you can automate some or all the tasks associated with SOC 2 compliance. You can even create custom policies that reflect your organization’s needs and manage risks in a single platform. Secureframe also offers training modules to ensure that your employees understand the requirements of SOC 2 compliance.
Expert Auditors
Secureframe partners with expert auditors who can accurately assess your current compliance levels. Based on this information, you can identify gaps and remediate them to get SOC 2 compliance.
Mapping of Security Controls
SOC 2 compliance has hundreds of security controls that must be implemented within your organization. Secureframe eases this implementation by condensing them into eight simple steps.
Overall, Secureframe is a comprehensive tool for managing SOC 2 compliance.
Pros:
- Integrates with AWS and GitHub for quick identification and remediation.
- Eases the compliance process.
- Responsive customer support.
- Comprehensive insights.
Cons:
- Learning curve for users.
- Training and documentation can be better.
10. Scrut
Scrut is a security and controls platform that enables you to comply with SOC 2 guidelines and principles. It oversees the various risk aspects related to your operations, identifies them, and helps you take the necessary steps for remediation, eventually leading to SOC 2 compliance.
Source: Scrut
Below are the Scrut features that can help with SOC 2 compliance.
Compliant Policies
Scrut makes it easy to create SOC 2-compliant policies using its 50+ pre-established templates. You can simply pick one of the tools and customize it within minutes to meet your organization’s specific needs. Scrut’s in-house specialists can even view your customized policies to ensure compliance.
Optimized Workflows
You can optimize compliance workflows through the Scrut platform by creating tasks, assigning them to individual employees, and monitoring their progress. It even supports collaboration among your employees to speed up the compliance process.
Automated Evidence Collection
Scrut offers 70+ integrations with popular tools for collecting evidence of compliance from them. It also stores all the collected data in a central place for easy analysis and future reference.
In all, Scrut offers many convenient features to help your organization comply with SOC 2 guidelines.
Pros:
- Unified view of risks in real-time.
- Extensive policy library.
- Built-in editor for easy customization.
- Single source of truth.
Cons:
- The user interface can be better.
- Limited alerts.
Thus, these are some of the best tools that can take your organization closer to SOC 2 compliance. While there are many similarities in their features, make sure to pick a tool that fits your budget and tech stack.
Bottom Line
In all, SOC 2 compliance is a voluntary specification, though many organizations prefer to become compliant with its provisions because of the credibility and trust that comes with SOC 2 compliance. There are five key principles that organizations must follow to become SOC 2-compliant, and all of them revolve around safeguarding sensitive customer data from data breaches and unauthorized access.
The tools we talked about in this article help with SOC 2 compliance. They come with pre-defined templates, extensive report generation, and risk assessment capabilities that can help your organization protect sensitive data. However, not all tools are built the same, and hence, evaluate each against your organization’s specific needs to pick the right one.