As data surges every day, protecting it from unauthorized access and misuse is becoming more complicated. It is estimated that the volume of data created in 2024 will be 147 zettabytes. For comparison, the data generated in 2013 was a mere nine zettabytes. While more data is good from an organization’s standpoint, as it gives them more insights into customer background and behavior, storing such large data volumes and safeguarding them requires a concerted approach.
Organizations must implement a wide range of solutions to ensure that their sensitive data like credit card details, customer details, and other information don’t fall into the wrong hands. One such solution is to use data protection software.
Below are the top ten best data protection software:
- Acronis Cyber Protect An integrated cybersecurity platform that offers streamlined data protection for IT teams and managed service providers.
- Hitachi Vantara Data Protection Suite An enterprise solution for long-term data retention and protection.
- Prisma Cloud Data Security A scalable tool for managing and protecting data in the public cloud.
- Bitdefender GravityZone A business antivirus software that can encrypt and decrypt data across multiple IT infrastructure models.
- Eperi Gateway A cloud data protection tool that encrypts all the data stored in the cloud while providing complete control over their access and usage.
- Nightfall AI An AI-native DLP platform to classify and protect sensitive data on SaaS and cloud apps.
- Infrascale A Disaster Recovery as a Service (DRaaS) platform that protects data and applications from ransomware, malware, and other cyberattacks.
- Thales A comprehensive data protection solution that keeps your data safe from evolving threats while ensuring compliance with relevant standards.
- Commvault Cloud A zero-trust data security platform that meets the security demands of a hybrid enterprise.
- Arcserve UDP A unified data protection software that safeguards your data from ransomware without the complexity of setup and management.
What is Data Protection Software?
As the name suggests, data protection software safeguards your sensitive data from theft, loss, or misuse. In the process, they also help you meet regulatory compliance as the laws surrounding data usage and protection are stringent.
These tools come with features like encryption, access controls, data backup, and threat detection. With the right data protection software, you can prevent external attacks, detect and neutralize insider threats, reduce the chance of errors in data handling, and more, depending on the software’s capabilities.
While it’s not possible to find software that’s comprehensive in every sense, you must identify a tool that best fits your organization’s infrastructure setup, compliance requirements, data storage practices, and budgets.
We have narrowed down this list for you.
Our Methodology
We evaluated many data protection software to pick our top ten. The criteria we used are:
- Availability of data discovery and classification tools to identify your organization’s sensitive information.
- Monitoring capabilities to check access and usage patterns.
- Risk analysis
- Automated reporting and dashboards
Best Data Protection Software
Now, let’s delve into each of our best data protection software.
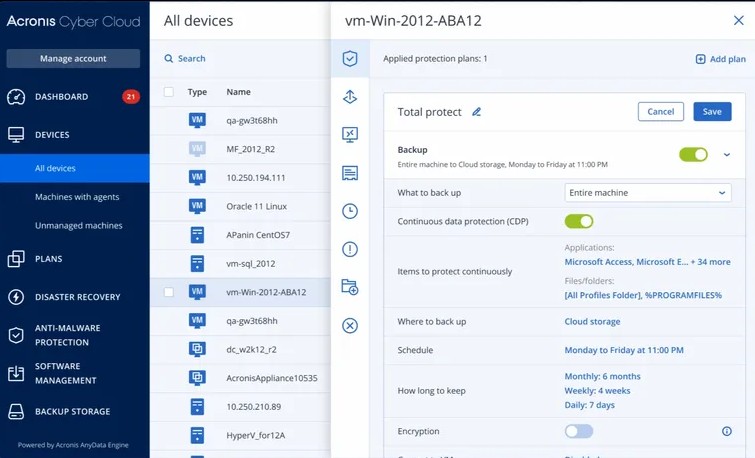
1. Acronis Cyber Protect
Acronis Cyber Protect is a complete data protection tool connecting cybersecurity with data backup and recovery. It strengthens the overall data resilience of your organization while helping you comply with data security standards.
Source: Acronis
Here’s a look at Acronis’ data protection features.
Improves Efficiency
Acronis automates the backup, security, and endpoint management tasks to improve your employees’ productivity, as they can focus on the more important tasks. Also, it centralizes the data protection activities to provide comprehensive visibility and control and to give your authorized employees the big picture. You can even use this centralized visibility to consolidate vendors and backup solutions for improved cost efficiency.
Boosts Security
Extensive security features like immutability and backup scanning help detect ransomware and prevent its impact on your data. Also, it employs an informed response and investigation approach to stop threats before they cause downtime. Its anti-malware protection and URL filtering add more security layers to your data protection strategy.
Simplifies Administration
Often, the administration of your security strategies is the biggest overhead. Acronis addresses this concern with its effortless scalability and consolidated views. With this tool, you can get instant notifications and the information required to promptly remediate issues.
With such features, Acronis Cyber Protect offers multiple layers of security while maintaining resilience and compliance.
Pros:
- Integrates backup, storage, and protection.
- Offers powerful ransomware and malware protection.
- Works well for organizations that want to protect sensitive information on remote PCs and mobile devices.
Cons:
- The mobile app is available for the higher-paid plans.
- Customer support can be better.
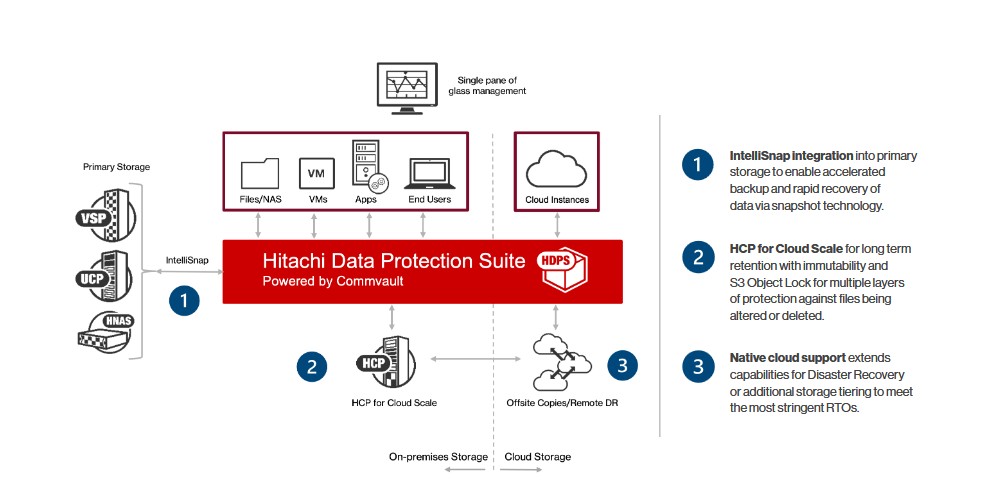
2. Hitachi Vantara
Hitachi Vantara is a heterogeneous data protection suite that protects and manages your sensitive information through a single interface. It is a consistent way to identify and manage your enterprise data spread across files, apps, servers, and user devices.
Source: Hitachi Vantara
Let’s look at the important Vantara features related to data protection.
Backup and Recovery
This data protection suite provides comprehensive data recovery and backup options for various environments, including virtual, physical, and cloud-based systems. With this tool, you can safely store your sensitive content and retrieve it when needed, especially in the event of a data loss or system failure.
Data Deduplication and Compression
Hitachi Vantara uses advanced data deduplication and compression techniques to optimize storage and reduce the associated costs. It can also eliminate redundant data and compress storage without data loss. This feature is particularly helpful for businesses that have to store and maintain large data volumes.
Centralized Monitoring
Vantara’s centralized monitoring and management capabilities provide comprehensive visibility into data across your entire organization. It also streamlines workflows, helps configure security policies, and generates reports that help compliance with leading data protection standards.
Overall, Hitachi Vantara enables organizations to safeguard data assets, mitigate risks, and maintain business continuity.
Pros:
- Stable and reliable.
- Easy to use.
- Scalable and configurable.
- Reduces design complexity.
Cons:
- Steep learning curve.
- Customer support can be better.
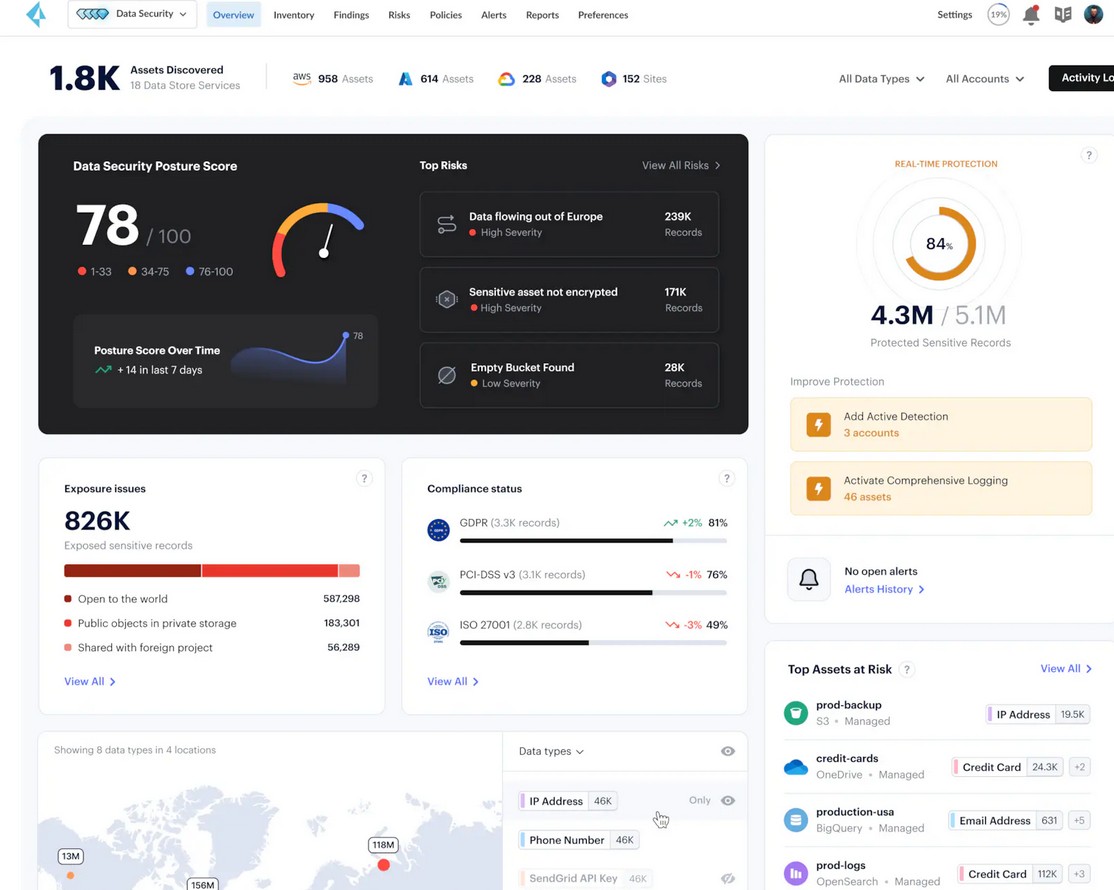
3. Prisma Cloud Data Security
Prisma Cloud is a cloud-native security solution from Palo Alto Networks that can secure your cloud environments and data. It offers Cloud Security Posture Management (CSPM) and Cloud Workload Protection (CWP) for multi-cloud environments, including AWS, Azure, and Google Cloud. More importantly, you can manage all your cloud data through a single interface.
Source: Palo Alto
Below are the features of Prisma Cloud Data Security.
Data Discovery and Classification
A highlight of Prisma Cloud is its data discovery and classification functionality that identifies sensitive data and classifies them into different buckets. It continuously monitors the data stored on AWS, Azure, GCP, and Snowflake platforms to find shadow and misconfigured data.
Privacy and Compliance
Prisma Cloud identifies the sensitive data while at rest and in transit. It monitors data flows across storage locations and environments to help you see the full picture for compliance. You can also see the specifications that can make you non-compliant, like moving healthcare records into unencrypted storage. Armed with such information, you can ensure data privacy and compliance with leading standards.
Data Detection and Response
Complex IAM policies and cloud sprawl can make it difficult to detect problems in your cloud data. Moreover, these aspects can’t prevent critical incidents. But with Prisma Cloud, you can detect and respond to high-priority incidents in minutes. Its agentless and dynamic monitoring can identify issues and notify you for instant actions.
With the above features, you can have better control and visibility into your cloud data, and protect it from unauthorized access and cyberattacks.
Pros:
- Ensures compliance with industry regulations and internal security policies.
- Offers pre-defined templates to help with compliance.
- Continuously monitors data to detect and prevent threats.
- Provides centralized visibility and control over cloud assets.
Cons:
- Not ideal for organizations with diverse infrastructures.
- There can be performance lags when processing high data volumes.
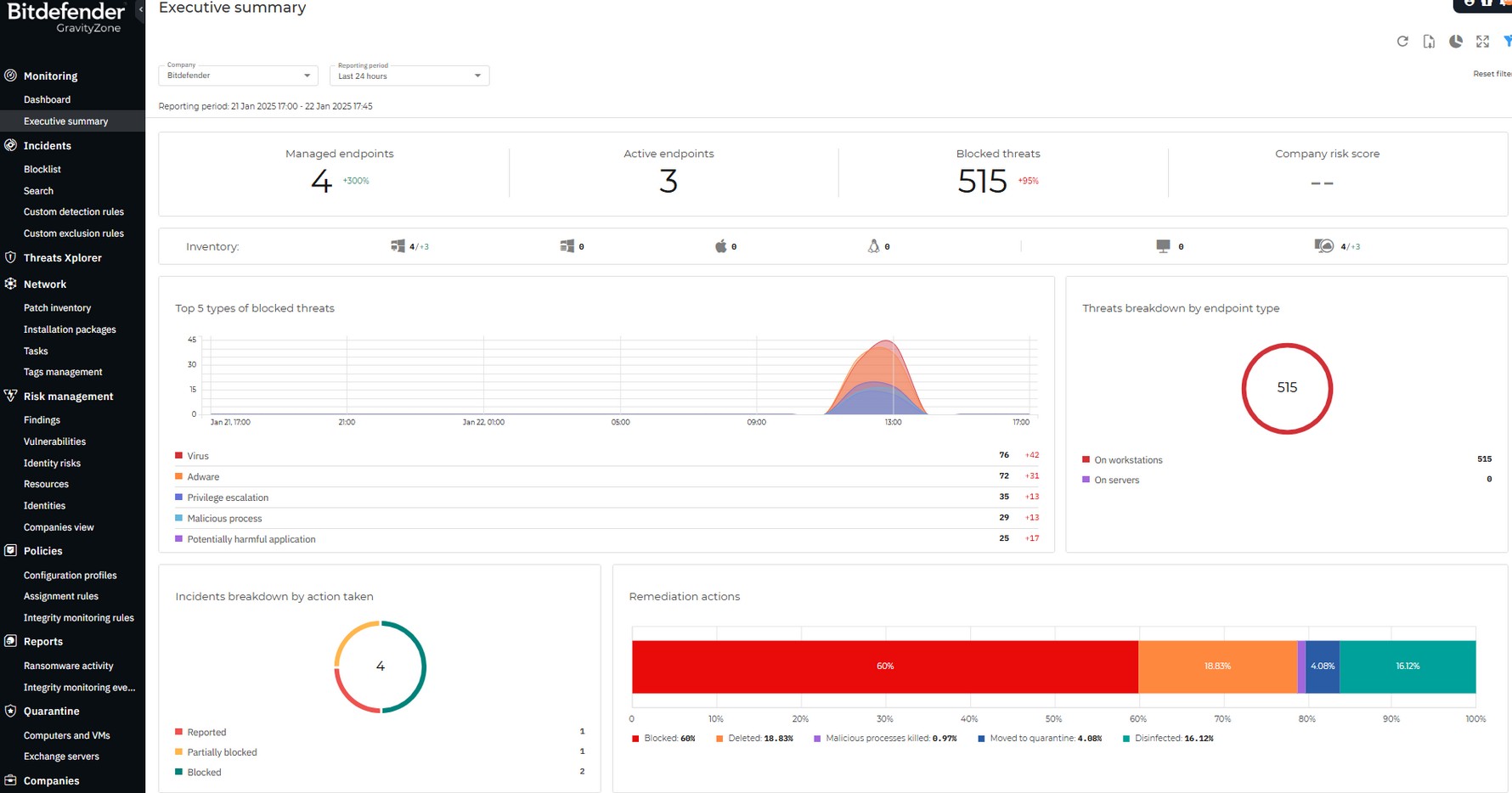
4. Bitdefender GravityZone
Bitdefender’s GravityZone is an enterprise antivirus solution that offers multiple layers of security for your data. It combines many techniques like system hardening, threat prevention, behavioral analysis, machine learning, detection technologies, and more to keep your data safe.
Source: Bitdefender
Below are Bitdefender’s data protection features.
Antimalware
Malware is one of the leading sources of data theft and breach that could result in millions of dollars in fines and lawsuits. Bitdefender’s anti-malware uses advanced security mechanisms to reduce the chances of such data breaches. It uses content scanning and heuristic analysis to identify potential malware before they get to your data.
Advanced Threat Control
Bitdefender’s advanced threat control continuously monitors your processes and identifies any suspicious activities like hidden or disguised processes, unauthorized code execution, privilege escalation, and more. It notifies these threats and provides the context to help you fix them quickly.
HyperDetect
HyperDetect is an advanced data protection technology that uses machine-learning models and stealth attack detection mechanisms to protect your data against cyber threats. It can identify a wide range of common threats and even zero-day attacks.
Besides the above features, Bitdefender also provides extensive visibility and control of your data handling activities. Its detection and response capabilities are also handy.
Pros:
- Centralized management of data and activities.
- Malware detection and remediation.
- Well-developed endpoint detection and response.
- Supports hybrid deployment
Cons:
- The configuration process can be complicated.
- It would be great to have a notification system specifically for malware.
5. Eperi Gateway
Eperi Gateway is a data protection platform that provides complete control over your cloud data. It encrypts sensitive information and ensures that only authorized users can decrypt and access them.
Source: Eperi
Here’s a look at Eperi’s data protection capabilities.
Encryption
Encryption is a key feature of Eperi Gateway as it ensures comprehensive data protection and control over your sensitive data. At the same time, you have the required agility, as it supports the anonymization and pseudonymization of your tokens.
Flexibility
Eperi Gateway is a highly flexible solution, as you can decide which data must be encrypted or tokenized. Also, you can deploy it on-premises, virtualized environments, containers, cloud environments, and more. Moreover, its patented templates support all major cloud applications as well.
Compliance Standards
Eperi is a European company that strictly prohibits back-door entry by third-party cookies. Also, its centralized enforcement of compliance standards provides a single point of control for all your activities. With this tool, you are one step closer to GDPR compliance.
Overall, Eperi Gateway encrypts your sensitive information which requires minimum changes to your existing infrastructure.
Pros:
- Extensive encryption.
- Streamlined access controls and permissions.
- Complete control
- Complete data control.
Cons:
- Limited reporting
- Not enough features for on-premises data.
6. Nightfall AI
Nightfall AI is an AI-native Data Leak Prevention (DLP) platform that can discover, classify, and protect your sensitive data across your SaaS and cloud applications. It also comes with pre-built templates that work well with SaaS products to minimize configurations.
Source: Nightfall AI
Let’s look at Nightfall AI’s key features.
Protects Sensitive Data
Nightfall AI discovers, identifies, and classifies sensitive data using machine learning algorithms. It uses detectors to scan data across hundreds of different files to identify PII, PCI, PHI, and other sensitive data. It can also undertake scans of historical data to identify hidden risks.
Automates Compliance
This tool automatically monitors non-compliance risks and pinpoints them. As a result, organizations can streamline and triage incidents by the guidelines of HIPAA, ISO 27001, GDPR, CCPA, SOX, FedRAMP, and more. It also consolidates reporting easing the annual audit process.
Creates a Culture of Safety and Compliance
Nightfall AI creates a culture of security and compliance with its automated notifications and coaching modules. You can use the real-time data offered by this tool to enhance your employees’ security awareness.
Overall, Nightfall AI leverages the developments in the AI and ML space to protect your data and help your organization comply with regulations.
Pros:
- Excellent customer support.
- Integrates with many tools.
- Ease of use.
- Seamless identification and classification of sensitive data.
Cons:
- Steep learning curve.
- The alert system can cause fatigue, especially if not configured well.
7. Infrascale
Infrascale provides extensive protection for your cloud data and applications with its comprehensive data backup and recovery features. Also, it uses strong practices to ensure that your data is always safe and protected.
Source: Infrascale
Let’s see how Infrascale’s features can protect your data.
Extensive Technical Controls
Infrascale uses various technical controls to safeguard your data. Its physical security measures like CCTV cameras and biometric access prevent unauthorized access while features like encryption offer virtual protection.
Change Management
Changes can open up risks for your data, which is where Infrascale’s change management features come in handy. It uses features like a multi-level approach to data access to protect data during changes. Also, it enables the creation of a multi-disciplinary board to oversee these changes.
Logging and Monitoring
Infrascale logs and monitors every data access and usage. It even has automated alarms to identify critical issues that can impact the confidentiality, safety, and availability of your sensitive data. Moreover, it’s easy to create tickets for every alert and monitor their progress.
In all, Infrascale protects your sensitive data located on-premises or in the cloud. It also helps to achieve ISO 27001 certification.
Pros:
- Built-in email notifications.
- Supports backup replication.
- Responsive customer support.
- Good replication and recovery options.
Cons:
- Steep learning curve.
- More deployment options will be helpful.
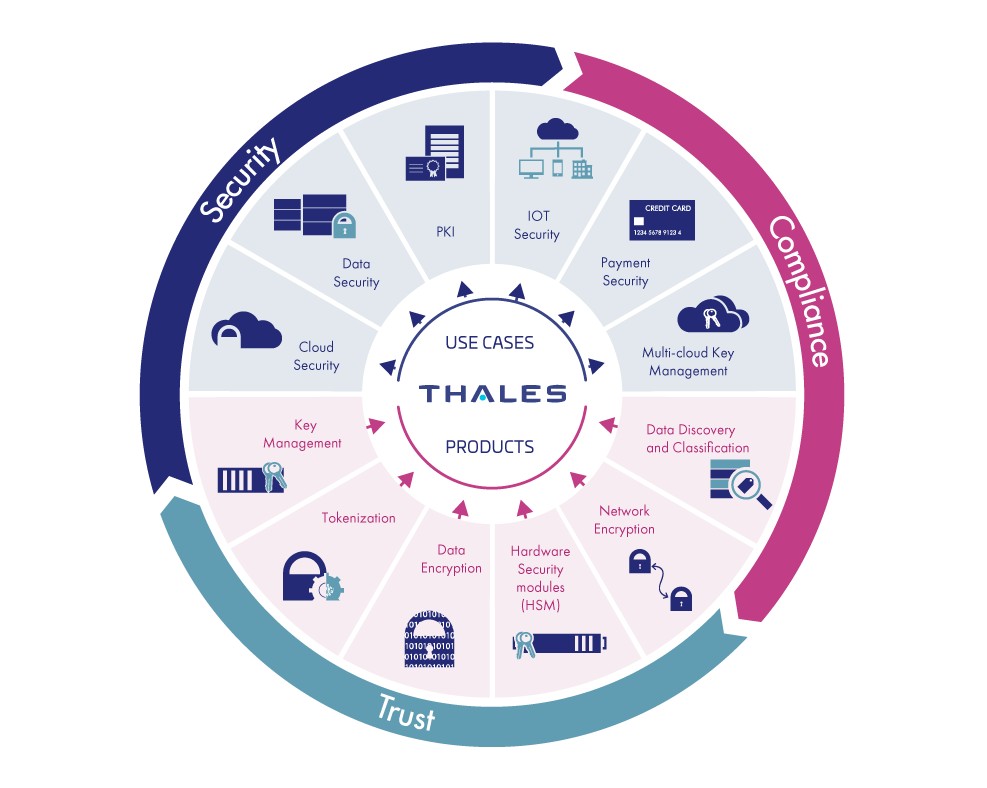
8. Thales
Thales is a data protection solution that offers a suite of products to discover, classify, and protect your sensitive data. It also comes with many features like data at rest encryption, key and secrets management, secure file sharing, and more to ease the data protection and compliance processes.
Source: Thales
Below are Thales’ data protection tools.
Data Discovery and Classification
Thales CipherTrust Data Discovery and Classification module can classify your sensitive data across different data stores for risk analysis. The advantage of this tool is that it is simple to use and can provide a clear understanding of what sensitive data your organization currently has and where they are stored.
Secure File Sharing
The SureDrop module enables secure file sharing and collaboration. It enables employees to share files with internal and external stakeholders. SureDrop uses standard encryption methods and integrated key management capabilities to send data and files securely.
Data Encryption
Thales offers granular encryption and role-based access control for both structured and unstructured data stored in databases, files, applications, and other storage containers in your organization. Also, its centralized key management practices ensure that the master key remains protected always.
With such security-focused features, Thales secures the sensitive data stored across your organization.
Pros:
- Simple to use.
- Useful validation and integrity features.
- Extensive and modular architecture.
- Supports single sign-on.
Cons:
- Dependency on Azure.
- Limited integrations.
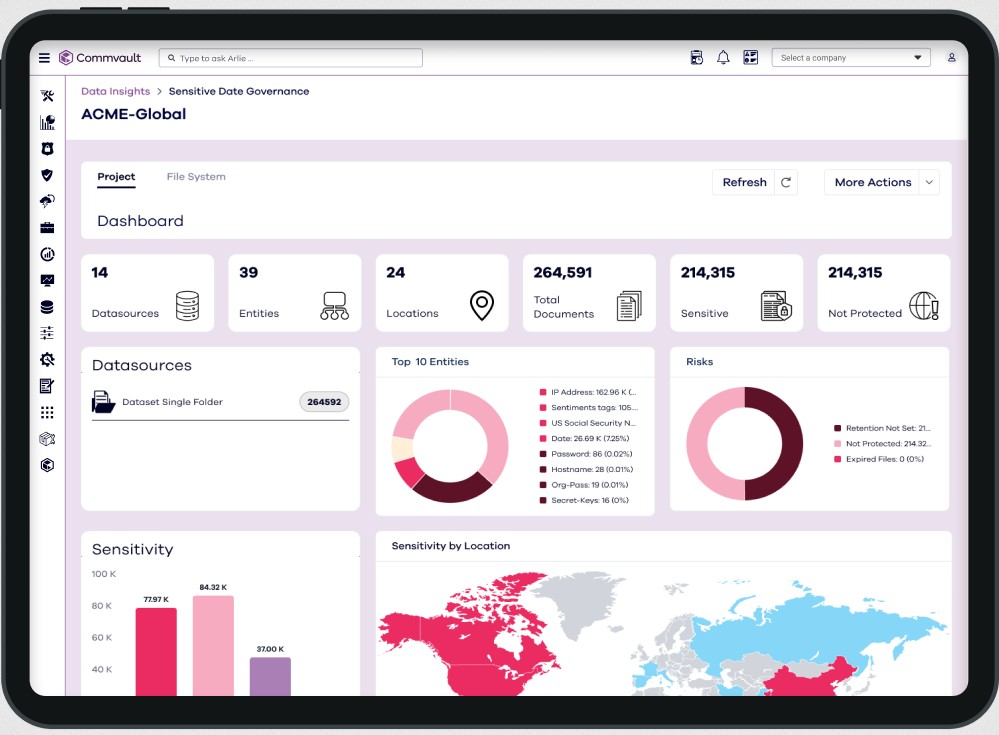
9. Commvault Cloud
Commvault Cloud is a zero-trust data security tool that protects your system and data from ransomware and other cyberattacks. It leverages the power of AI through its Metallic AI monitor to predict and prevent unauthorized access to your sensitive data.
Source: Commvault Cloud
Below are the salient features of Commvault Cloud.
Extensive Integrations
Commvault Cloud’s extensible and API integrations are overarching and enable you to identify data breaches, defend against them, and even recover from them quickly. You can even obtain data from multiple sources and analyze them for potential risks.
Simplified Management
The advantage of using Commvault Cloud is that you can see and control all data usage through a single pane. With such visibility, you can even improve your security while lowering the costs.
Risk Detection
Metallic AI, the proprietary AI tool of Commvault, uses machine learning and automation to identify risks like ransomware faster. Also, it provides the intelligence to identify and fix gaps before your sensitive data gets breached or stolen.
In all, Commvault Cloud offers widespread data protection against emerging cyber threats using advanced AI and ML techniques.
Pros:
- Flexible backup options.
- Excellent reporting.
- Easy to use
- Flexible, with its API-based integrations.
Cons:
- Alerts can be more intuitive.
- The restoration process is not seamless, especially for databases.
10. Arcserve UDP
Arcserve Unified Data Protection (UDP) unifies data across your organization and protects it from ransomware and other cyberattacks. At the same time, it simplifies data management and provides comprehensive control and visibility over the use of sensitive data.
Source: Arcserve
Here are the notable features of Arcserve.
Cloud-Based Console
Arcserve’s cloud-based console simplifies data management and protection. It is easy to configure and supports granular access control. Plus, the interface is easy to use and provides a single source of truth for data usage.
Multi Platforms
It supports multiple platforms including Microsoft, VMware, Nutanix, Red Hat Linux, Oracle, Debian, Ubuntu, and more. Moreover, it is the critical data stored in databases like SQL Server, Oracle, and more.
Smart Dashboards
The one-view dashboard displays insightful views and detailed information on the protected status of your sensitive data. Armed with these insights, you can create appropriate usage policies when required.
Overall, Arcserve provides resilience for your data while enhancing the availability and accessibility to authorized users.
Pros:
- Works well for organizations of all sizes and industries.
- Good technical support.
- Ensures high data availability.
- Stable and reliable.
Cons:
- May require additional resources.
- Limited manuals and documentation.
Thus, these are the best ten data protection software.
Bottom Line
Data is one of the most valuable assets for any organization today, hence it’s important to take all possible measures to protect it from unauthorized access, theft, and loss. While there are many strategies to safeguard, a comprehensive data protection platform can be a good starting point. In this article, we looked at the best ten data protection tools and we hope you use this information to identify the best fit for your needs.