Got an email from the Web Security Team re suspicious log in activity? Careful where you tread because one click could break the ice! A case study in phishing and email spoofing
If you are a small startup like us, there are plenty of things that keep you busy. Product development, people management, infrastructure, financing, marketing and to make matters worse we keep telling you to bear legal and compliance issues in mind. Juggling all these balls, you might feel stressed and when an email comes along that warns you of an imminent breach of your security systems and you might be a little trigger happy. But one click can bring the whole house down that you constructed so carefully. We are talking about phishing attacks and since we were subject to one, we thought we better share it with you, tell you what to watch out for and how to limit the risk as much as possible.
You might have guessed it but Phishing comes from password and fishing and refers to the attempt to lure people into sharing confidential information like logon or credit card details with fraudsters. In most cases it’s done by sending an email with a fake sender address misleading the recipient about the origin of the message. It could be from a bank telling you to urgently log on to approve a payment or complete security verification. It could come from an online marketplace or your email provider about expiring password. It’s called email spoofing but phishing also works with instant messaging and social media. Mobile phishing is on the rise and because we often respond faster, especially if we know the sender, it makes platforms like Whatsapp even more attractive for criminals using phishing techniques.
And the consequences can be catastrophic! Phishing is one of the most common ways of cybercrime, in fact, according to reports from the Anti-Phishing Working Group (AWPG), 76% of surveyed organisations stated that in 2017 they had experienced phishing attacks with its latest report showing that the number of phishing attacks rose in the third quarter of 2019, to a high level not seen since late 2016. For financial services firms such attacks can be exceedingly expensive as the average cyber attack on average costs a company $18million. For the regular startup this can easily mean it has to close shop.
While security software is in a constant arms race with cyber attackers, most e-mail software is not capable of verifying an email address and who has sent the message. Instead it simply transmits what the sender enters in terms of information. As we have demonstrated in a recent post, anyone could send an email pretending be to be Bill Gates, Elon Musk or anyone else by simply editing the information shown on the outgoing mail.
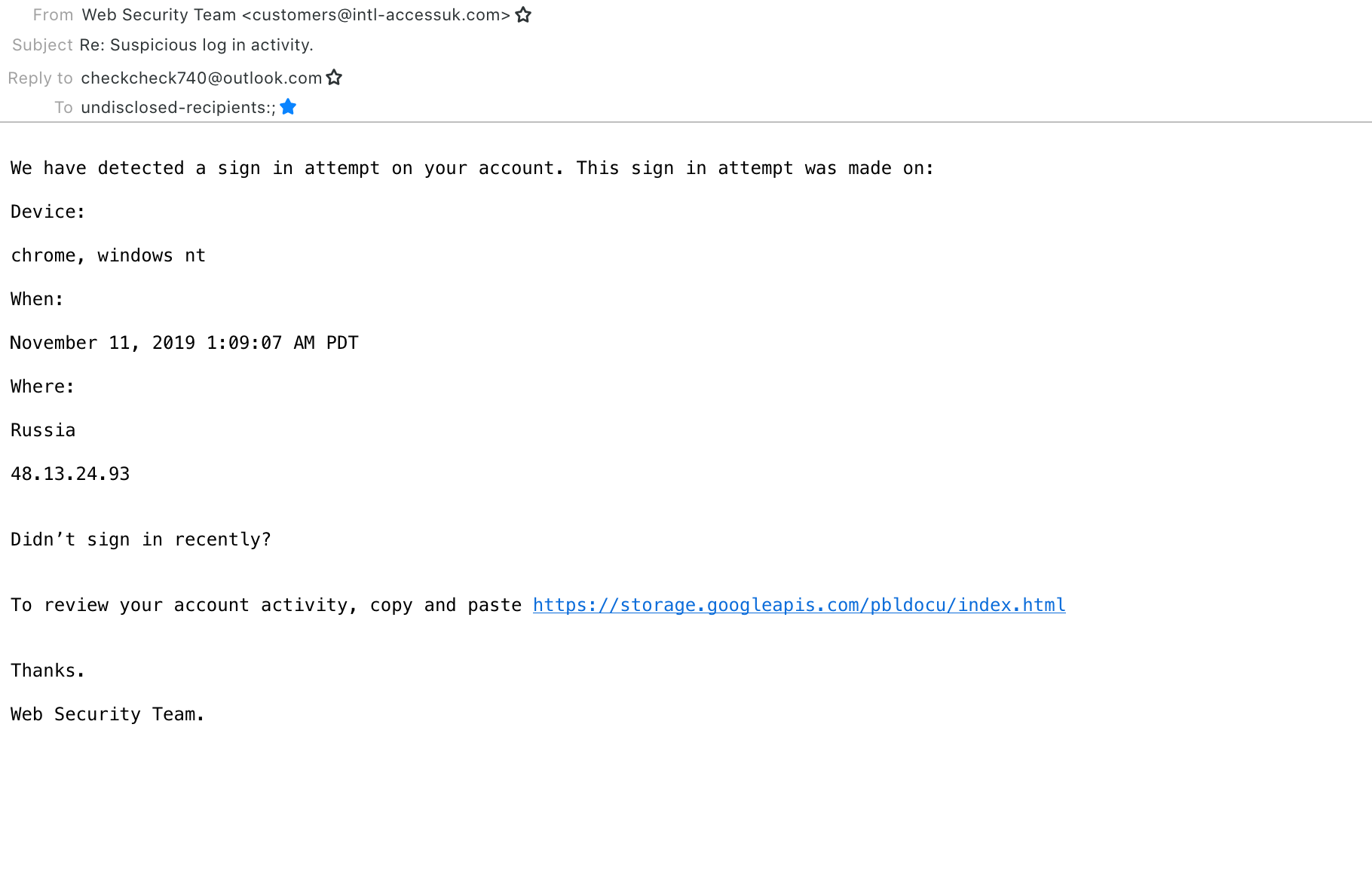
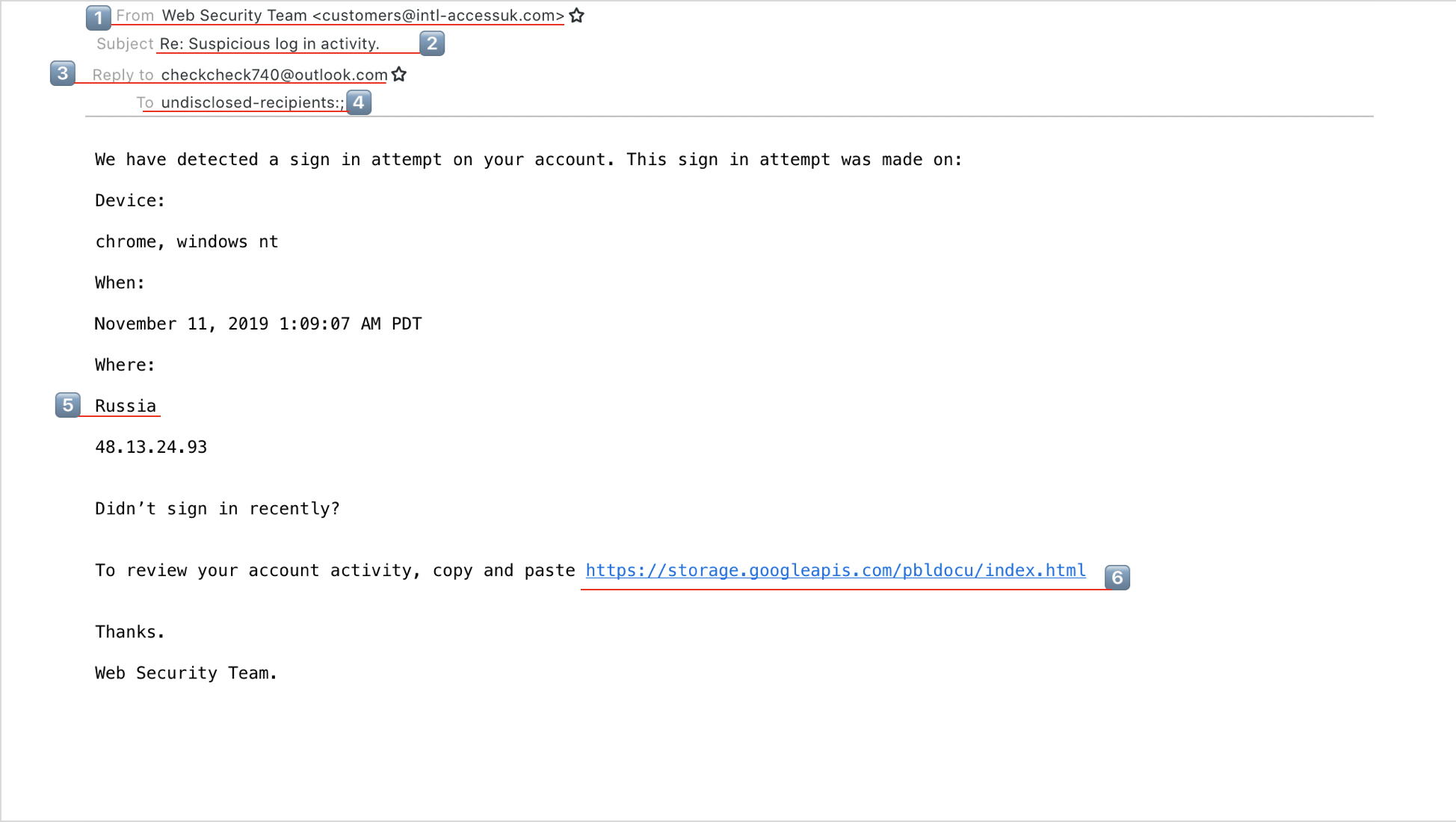
With this in mind the best defence is awareness and education. That’s why we’d like to share the following email that found its way into one of our mailboxes this morning and looked a tiny bit suspicious:
So, what do you think? Any thoughts on the suspicious elements? No? Well, let’s go through some of the red flags that made us decide eliminating it immediately:
- To start with, if you look up intl accessuk, you’ll be disappointed. We couldn’t find any such company and it already looks a bit strange that the Web Security Team should send emails from its “customers” account, doesn’t it?
- “Re: Suspicious log in activity” – Why re:? In response to what? Re: indicates that there is an ongoing conversation, aiming to create trust since this must people we have already been in touch with, haven’t we?
- If this is a genuine company, why would I have to reply to a free outlook email address?
- “To: undisclosed recipients” – either there is a massive data breach at this company and they have decided to notify all at once (not good form, is it?) or this is simply sent to a list of email addresses the perpetrators have got from somewhere on the web. Unfortunately, the number of data breaches steadily increases, so it’s not very surprising that one of our email addresses ended up on one of these lists, too. Or it simply was discovered by a bot crawling website for email addresses it could scrap since it was the privacy contact we have published if someone is concerned. It certainly isn’t an address we used to sign up at Intl AccessUK… but if you are concerned about your own email address and you want to check the status of your account, have a look here.
- Where does this imaginary scam come from? Of course, Russia! We can’t rule out that the actual fraudsters sit in Russia, but if you wanted to dupe someone into believing that they are hacked, which country would you put there? Right.
- And for the grand finale, here is the link you’re supposed to click (or copy & paste) to review the suspicious activity, which supposedly is on a Google drive. Even if you really wanted to believe that there is nothing dodgy about a reputable company like Intl AccessUK directing us to its account management system on Google drive (it must be a real lean startup that cuts corners where it can to keep costs down, you’d assume), there is plenty to read about the weaponizing of Google Cloud Storage for phishing attacks or to spread trojans and other malware.
To summarise, plenty of red flags that made us stay clear from following the link and there certainly is more to discover. For example, you could review the source of the email in your email client, which might have shown further irregularities, but, frankly, we already had enough.
In this case, it was fairly easy to spot and you might have come across one of those wonderful examples, full of typos and grammatical errors. However, others are remarkably well crafted, taking you to a fake website that looks almost identical to the real thing. So, what should you do and always keep in mind? Here are a couple of things that should help you spot a phishing attempt:
- Grammar and spelling errors: We already mentioned typos, but the easiest way to discover fishy emails simply is a poorly drafted email. After all, do you really think that your bank can’t afford any one better than the person that wrote this email in broken English?
- Missing name: Wrong or no name at all indicate that it’s mass mailing like the our example from above. Keep in mind though that more sophisticated actors might actually be able to get part of your personal details and tailor their attack so it actually addresses you by name. If it really was your bank though contacting you, they surely would address you properly, right?
- Emails in a foreign language: Instantaneously recognizable as phishing are e-mails that are written in a foreign language and where you have never done business.
- Creation of urgency: The urgent need to act to avoid blocking of an account, for example, is one of the key elements of a phishing attack as it designed to lower your defenses. Rather than carefully consider the situation (and spot the hoax), it aims to tempt you into doing something rashly without fully thinking it through. Why else would click on a link sent from someone you don’t know and shouldn’t trust?
- Data input: Unlike trojans or other malware that consist of self-deploying files that infect your computer, phishing attacks want to extract sensitive information like your security number or credit card details. Banks frequently send out reminders that such information is never requested from financial institutions by phone or e-mail.
- Unknown sender: If you don’t know the person or organization that has sent you the email or you have never provided them with your contact details, just delete. In the worst case, it’s spam.
- Email header: Again, some phishing emails are actually well done. You might recognize the sender and the email address, the way the link is displayed looks genuine, too (though the way a link is displayed and the address that is actually linked to, can also be completely different!), and even the wording is perfect. Still, as we pointed out, everything can be faked – from the sender address, to links to the message itself. If there is an element of doubt, double-check! It’s better to be safe than sorry!
Naturally, there is plenty more aspects and elements we could consider here. It isn’t said either that cyber criminals find their ways around the basic safety rules we listed above, but it’s a good starting point and the fundamentals to protect your data.