Regulators warn against scams related to the Covid-19 pandemic seemingly on a daily basis. It is high time for cybercrime who try to take advantage in various ways of the Coronavirus crisis. Fake purchase orders and phishing attempts aren’t an invention made especially for the current emergency, but play perfectly to the uncertainty and confusion created by it. A practical example how crooks use the fake purchase order scam to gain access to your computer.
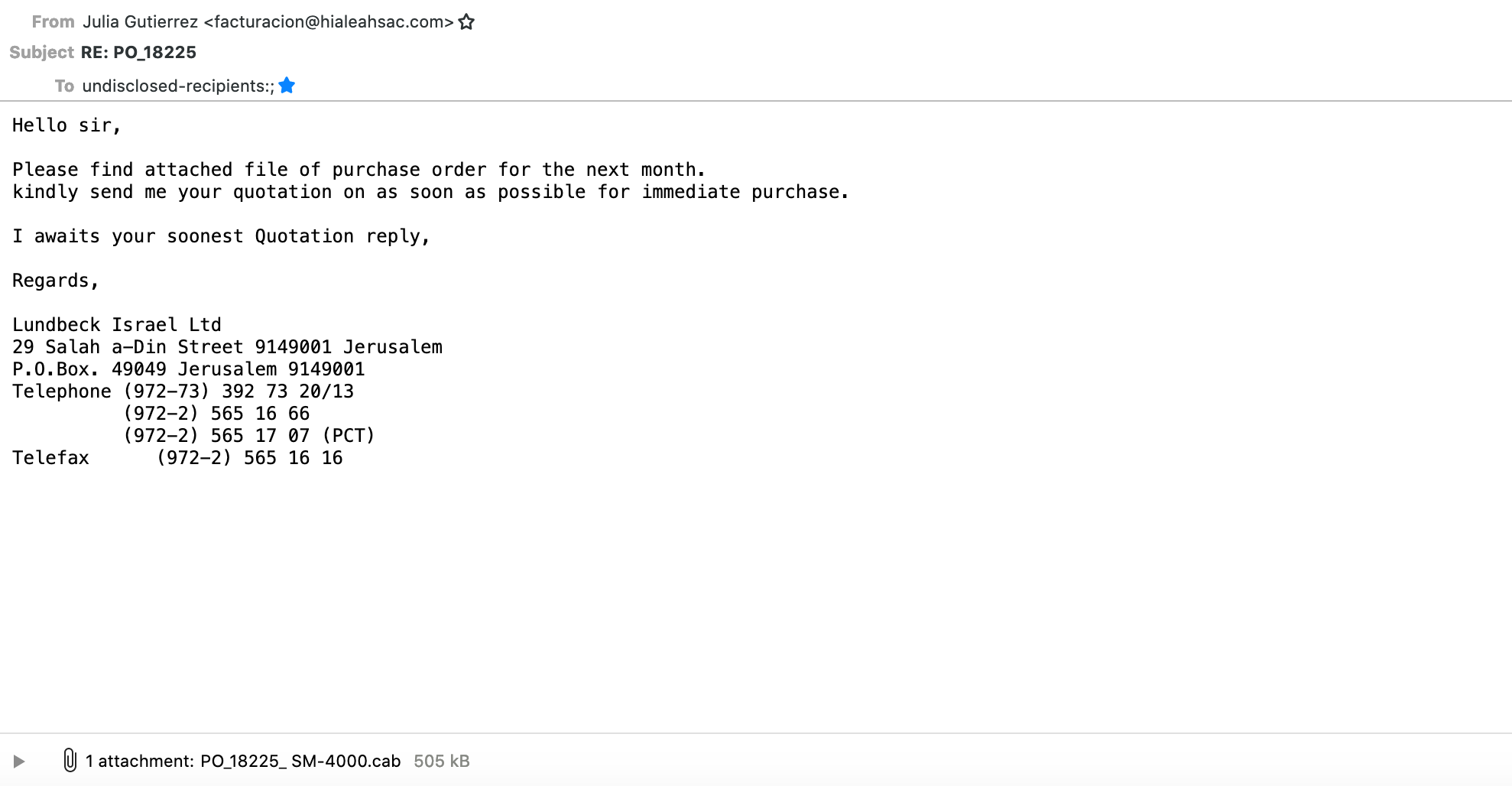
You’ve got mail! You know the familiar feeling when a notification flashes up somewhere on your screen. That probably happens dozens or even hundreds of times a day for you and many of the emails we receive should find their way directly to the bin. But sometimes something important pops up (literally if you have some kind of notification enabled) and catches your attention. Just like what happened with an email I’ve received the other day entitled PO_18225.
A new lead? An opportunity for new business? Or simply a recurring customer that needs an urgent confirmation? In any case, what appears like a welcomed injection of money in challenging times, is nothing else but a phishing attack disguised as a purchase order. Which, instead of bring you new business, is likely to cost you a lot of money if you are not careful.
While it may seem pretty obvious, unfortunately emails like these are surprisingly successful in their attempt to break a firm’s cyber defenses.
Fortunately, there several warning signals that should ring alarm bells and hopefully keep you from making a disastrous mistake. Right away six spring to mind, so why not make a game of it?
Here is the original, now can you find the six red flags? (You can, of course, simply scroll down and find out without the guessing if you are in a hurry)
You weren’t cheating and just scrolling down without giving a try, were you? Just kidding, go ahead!
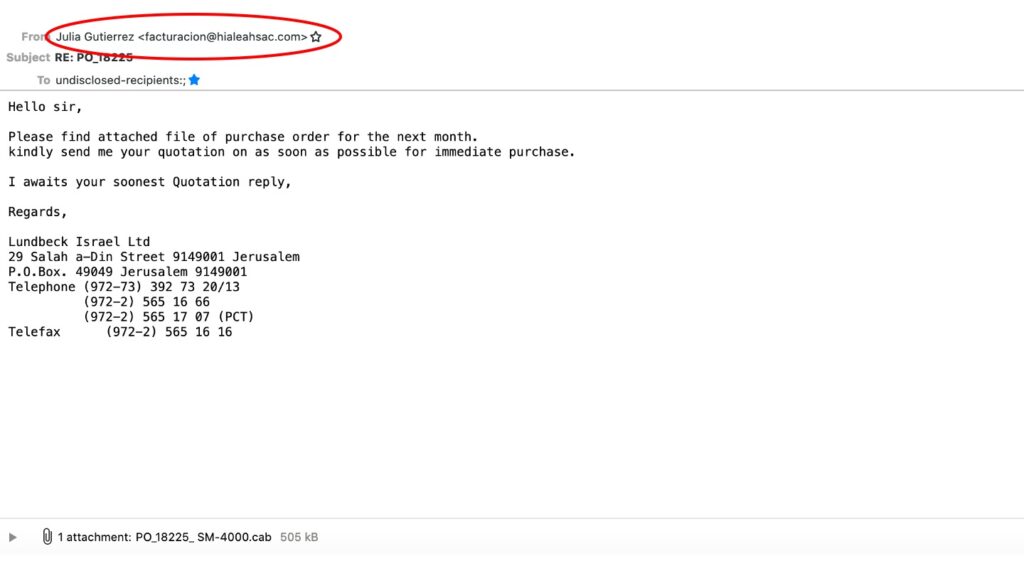
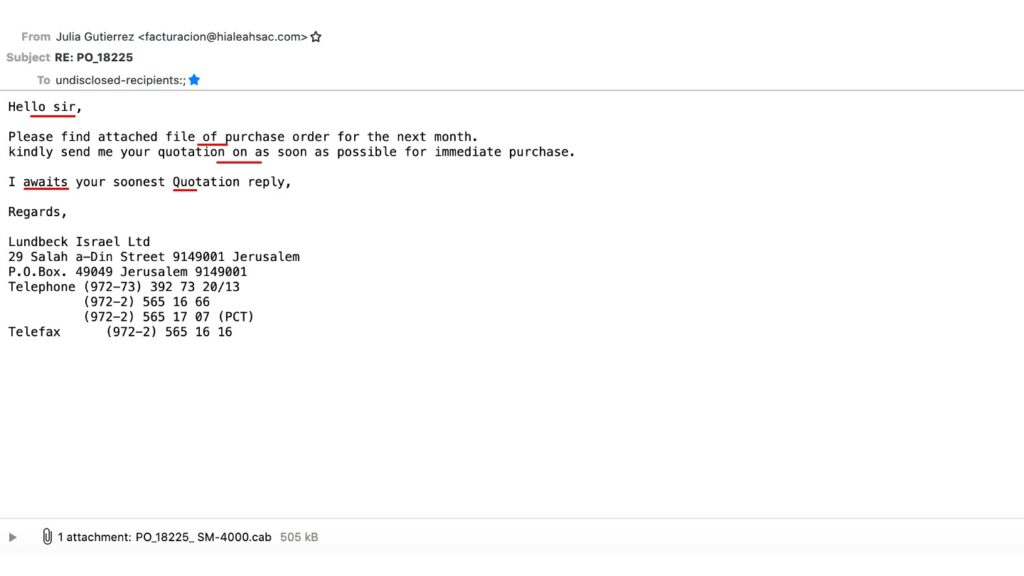
1. The first red flag is that the displayed name and the email address don’t match. It could well be that a woman named Julia Gutierrez works in accounting (I assume that is what facturacion means – my Spanish is a bit rusty), but why has the department a Spanish name.
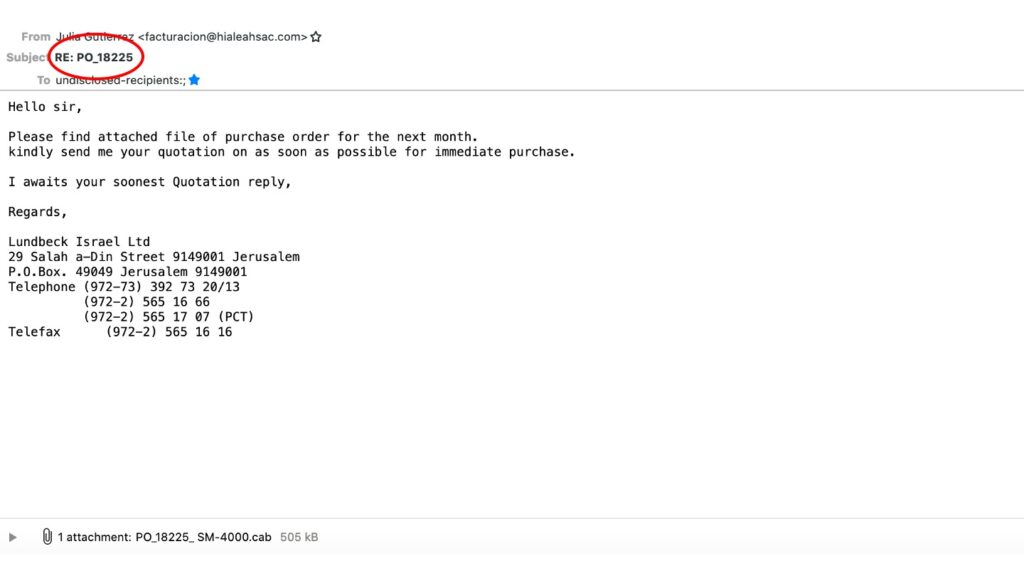
2. RE? RE: as in reply? In reply to what? Did I send an email with regard to a purchase order numbered PO_18225? Again, my memory might fail me or it could happen that I indeed am the person responsible for sales, but I’d better think twice, right?
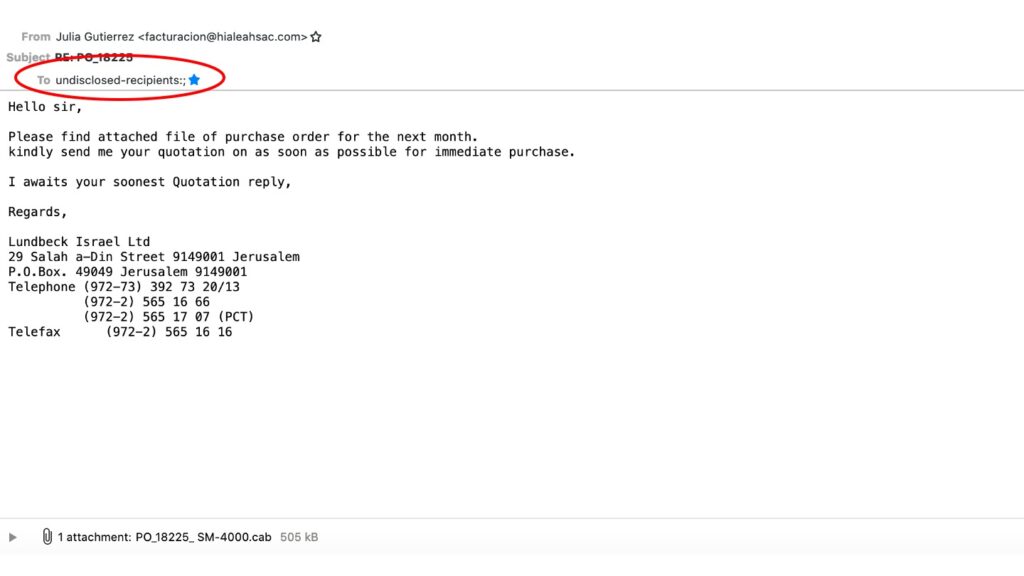
3. You’re probably not convinced yet and the evidence so far is a bit weak, so let’s move to the more evident stop signs beginning with: Undisclosed Recipients. Now that doesn’t make any sense anymore: why would someone send an email and choose not to display the recipients. That’s usually something you do if you send a message to a lot of people, isn’t it?
4. Language and typos: the email in question contains a number of misspellings and grammatical errors. That can happen in any email (and in fact happens more often than not), but if you look at a lot of phishing emails, you’ll find that such signs are a good indicator for dealing with people from countries that struggle with the orthography.
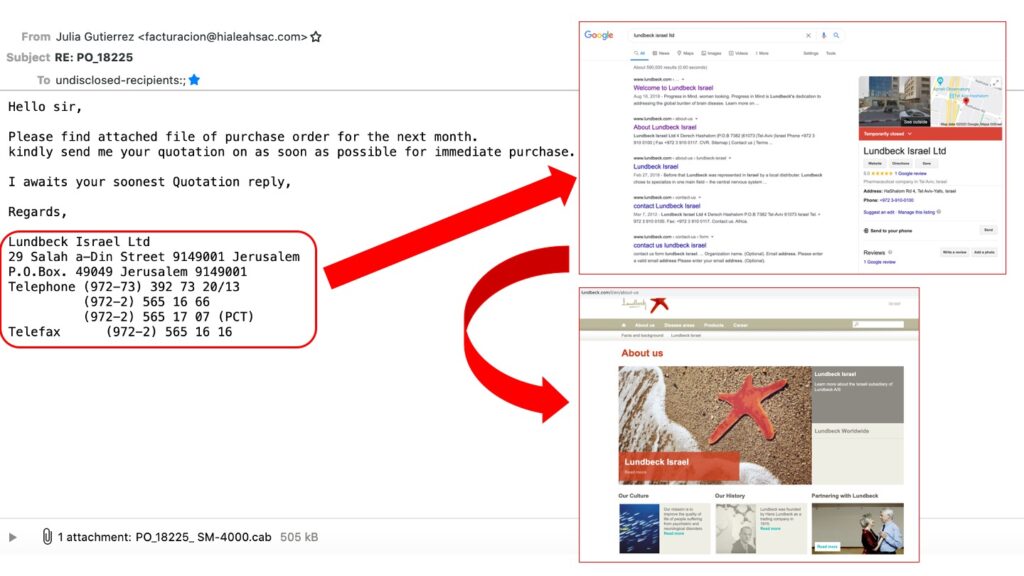
5. You’re still not convinced, are you? Okay, let’s look at the company that apparently would like to purchase something from us: Lundbeck Israel Ltd. A quick check reveals that Lundbeck is a pharmaceutical company, so the question is whether there is any chance that you would have any dealings or business with this company? The answer for me was a straight no!
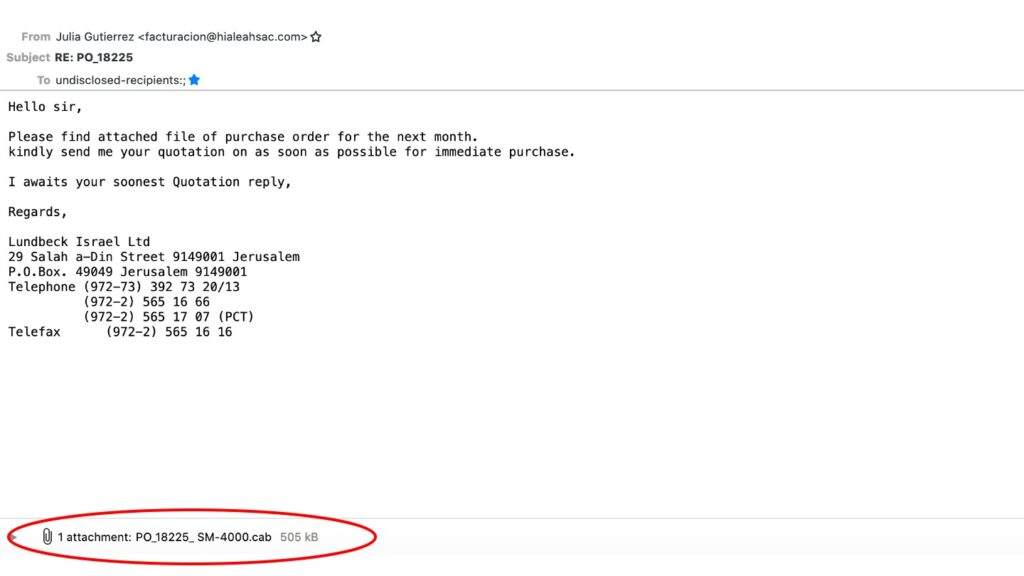
6. And lastly, the attachment and its file format: I’d say that a purchase order usually comes in word format or a PDF, but the file extension of this one is .cab. Another quick check reveals that it stands for Cabinet, which is an archive-file format for Microsoft Windows that supports lossless data compression and embedded digital certificates used for maintaining archive integrity according to Wikipedia. In case you didn’t know but it’s rather common to put the malware into a compressed archive because it is an easy way of bypassing your anti-virus/anti-malware software until the archive is decompressed.
Whenever someone sends you a file with a zip, rar or other file archive extension, the alarm bells should ring and you should ask yourself – even if you know and trust the sender – why they would send you such a file. It doesn’t take a rocket scientist to change the sent address on an email and fraudsters use this method frequently, so better think twice before you click.
Luckily, this email came with plenty of warning signals and I didn’t open the attachment, which was likely to contain some form of malware. Don’t be fooled though, because in many cases cyber criminals are more diligent, draft better emails and hide their tracks more efficiently. Stay safe, stay vigilant!