Organizations operate within complex ecosystems involving suppliers, partners, and customers. These supply chain networks, both physical and digital, are susceptible to various risks, including cybersecurity threats and supply chain disruptions. A weak link in this interconnected web can lead to significant liabilities, making it essential for organizations to identify and face potential risks proactively. Comparitech has a helpful worldwide software supply chain attacks tracker that is updated daily.
Here is our list of the best Supply Chain Risk Management tools:
- JFrog (EDITOR’S PICK): JFrog’s platform specializes in secure software supply chain management, ensuring the security of artifacts, authorizations, and dependencies.
- InsightAppSec (Rapid7): Provides web app vulnerability testing.
- GitLab: Offers static code analysis integrated with CI/CD pipelines.
- Circle CI: Optimizes test execution with parallelism support.
- CrowdStrike: Offers threat detection capabilities using behavioral-based analysis.
- Docker: Accelerates application building, testing, and deployment with containers.
- Wiz: Provides a comprehensive cloud security suite.
- TrustInSoft Analyzer: Offers formal verification for identifying software vulnerabilities.
- Hdiv Detection (Datadog): Features intuitive vulnerability identification.
- Snyk: Offers real-time vulnerability detection and remediation advice.
Supply chain risk management tools are indispensable for finding and mitigating vulnerabilities within supply chains. These tools provide tailored solutions to address specific risk factors across various industries. One critical area where technology excels is supply chain mapping solutions, offering comprehensive visibility into supplier relationships. In this area, tools focused on vendor risk management are essential for safeguarding against cyber threats originating from third-party vendors.
These tools enable proactive risk monitoring and mitigation, ensuring operational continuity and minimizing supply chain disruptions. For example, environmental risk-focused solutions leverage artificial intelligence to predict and respond to weather events, aiding industries reliant on transportation and logistics. Accurate forecasting minimizes transportation delays and mitigates losses due to adverse weather conditions. Other examples include geopolitical risk solutions, which utilize data analytics to assess and mitigate risks arising from geopolitical factors.
For companies that operate in the digital realm, code verification solutions safeguard against cyber threats stemming from third-party code integration. By assessing code for vulnerabilities before, during, and after integration, these tools ensure the security of proprietary systems and data.
Types of Supply Chain Management (SCM) Solutions
Continuous monitoring and evaluation of vendor cybersecurity posture enhance overall supply chain security and resilience. Industries such as finance, healthcare, and technology rely on these tools to strengthen cybersecurity defenses and mitigate third-party risks, ensuring compliance and protecting sensitive data.
Incomplete List of SCM Tool Types:
- Supply Chain Mapping Solutions: Excel in providing visibility into supplier relationships, facilitating proactive risk management.
- Environmental Risk Solutions: Leverage artificial intelligence and big data to predict and respond to weather events, minimizing transportation delays and mitigating losses.
- Code Verification Solutions: Safeguard against cyber threats by assessing code for vulnerabilities before integration, ensuring the security and integrity of digital systems.
- Geopolitical Risk Solutions: Utilize advanced data analytics to assess and mitigate risks arising from geopolitical factors, offering real-time insights for informed decision-making.
- Vendor Risk Management Solutions: Essential for safeguarding against cyber threats originating from third-party vendors, ensuring compliance and protecting sensitive data.
- Continuous Monitoring and Evaluation: Enhance overall supply chain security and resilience, particularly in industries such as finance, healthcare, and technology.
What Supply Chain Problems Do SCM Tools Solve?
Gaining access to one part of the supply chain allows hackers eventual access to many companies within the supply chain, allowing attackers to modify source code and conceal malware or backdoors in updates or designs. Once sufficient chaos has been created, cybercriminals have the ability to demand some type of ransom or retribution in exchange for relinquishing their access to the system. The tools we are reviewing today focus on a lot of different elements of protecting supply chains.
Supply chains face various risks, including cybersecurity threats and disruptions based on weather, unplanned outages, and staffing or materials shortages. Supply chain risk management tools are essential for identifying and mitigating vulnerabilities across industries, and these tools focus on many aspects of supply chain security.
Supply Chain Risk Management Tools: Mini Reviews
Here are some mini reviews of the best supply chain risk management tools.
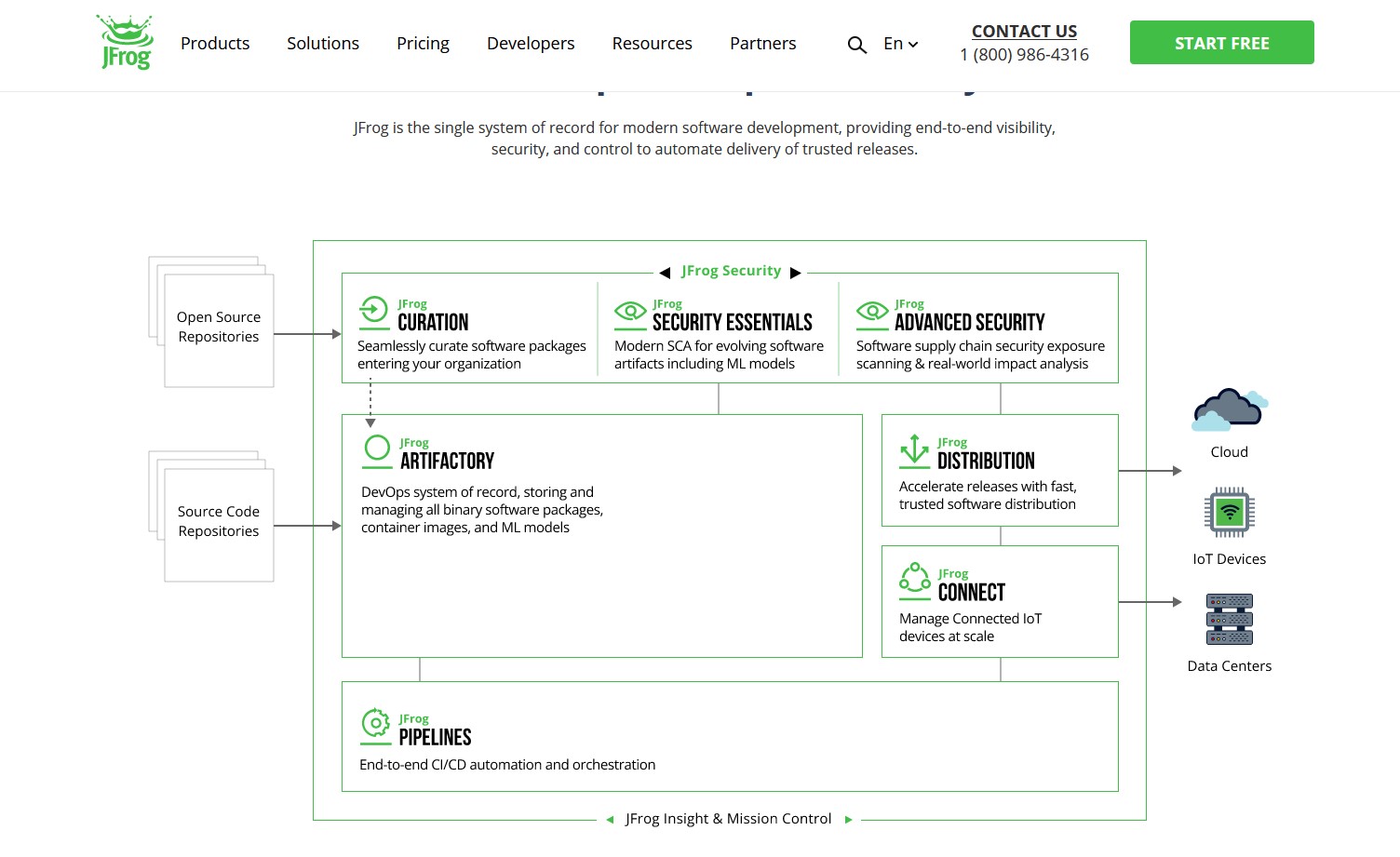
JFrog (EDITOR’S PICK, DEMO)
With features like artifact management via JFrog Artifactory and comprehensive vulnerability scanning with JFrog Xray, it’s essential for secure supply chain practices. JFrog is a widely respected IoT management system. The tool is especially useful for companies seeking a way to efficiently update firmware on Industrial IoT devices.
Key Features:
- Comprehensive software supply chain management platform.
- Secure artifact management with JFrog Artifactory.
- Vulnerability scanning and compliance checks with JFrog Xray.
Why do we recommend it?
JFrog offers a robust solution for managing software artifacts and dependencies throughout the development lifecycle, with strong security features and comprehensive vulnerability scanning.
Who is it recommended for?
Recommended for organizations seeking a secure and efficient software supply chain management platform.
Pros:
- Easy deployment and maintenance.
- Availability of training through JFrog Academy.
- Graph representation and vulnerability management.
- Detailed scan results with steps to reproduce code/function.
Cons:
- Resolving issues automatically doesn’t work effectively.
- Clunky user interface.
- Comparatively high false positive rate.
Pricing:
JFrog offers flexible pricing plans tailored to different needs. JFrog Connect provides IoT device management solutions starting from $0.30 per additional device. Customers can explore various support options, including 24/7 SLA Support and Platinum Support for further customization and assistance. The PRO plan, at $150 per month, suits small teams with Artifact and Container Registry features. The ENTERPRISE X plan, priced at $750 per month, is for larger organizations needing multi-site capabilities and advanced security. For comprehensive software supply chain management, the custom-priced ENTERPRISE+ plan offers distribution and higher uptime guarantees.
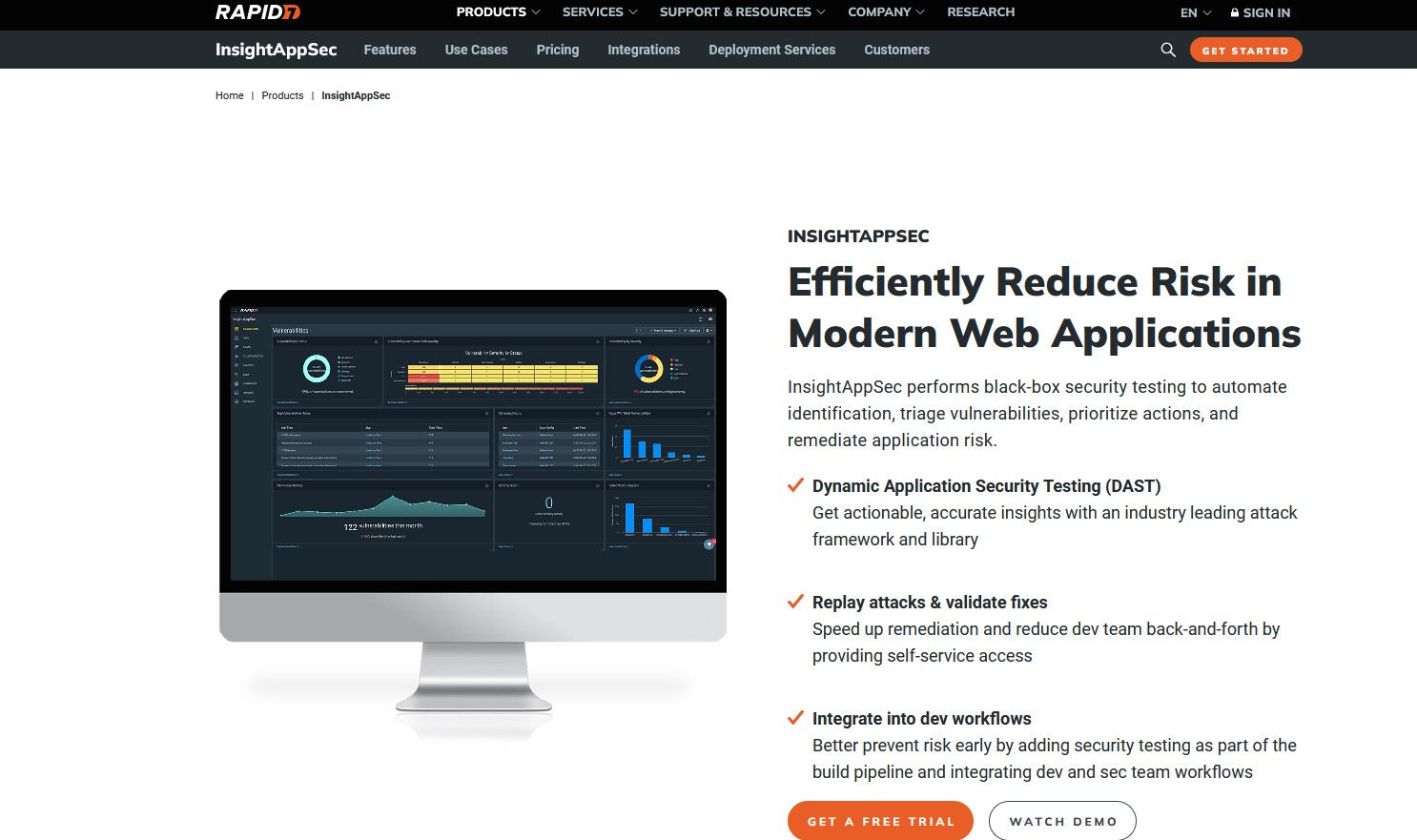
InsightAppSec (Rapid7)
InsightAppSec by Rapid7 provides thorough web app vulnerability testing, crucial for securing digital supply chains. Its detailed reports and dashboards facilitate collaboration between teams, enabling effective risk management across the supply chain.
Key Features:
- Guidance, standards, and frameworks for web app vulnerability testing.
- Comprehensive reports and dashboards for tracking remediation progress.
Why do we recommend it?
Rapid7 InsightAppSec offers a user-friendly solution for web app vulnerability testing with valuable reporting capabilities.
Who is it recommended for?
Recommended for organizations looking for a comprehensive web app vulnerability testing solution with robust reporting features.
Pros:
- Easy to deploy and maintain.
- Detailed scan results with steps to reproduce.
- Intuitive user interface.
Cons:
- Automatic resolution feature doesn’t work effectively for all cases.
Pricing:
InsightAppSec’s pricing structure offers flexibility to suit different needs. For up to 1 app, the cost is $2,400 for 12 months, with discounts available for longer-term commitments. For larger-scale usage, such as up to 5 apps, the price is $12,000 for 12 months.
There’s also an option for Total Risk Coverage, providing coverage for up to 5 “critical” apps at $54,000 for 12 months. Managed IAS and Custom Pricing options are available, with terms and coverage to be defined in Private Offers.
GitLab
GitLab offers robust static code analysis, vital for identifying and remediating code vulnerabilities in the supply chain. Integrated with continuous integration and continuous delivery/continuous deployment (CI/CD) pipelines, it streamlines development workflows, ensuring code quality and security throughout the supply chain.
Key Features:
- Static code analyzer with CI/CD integrations.
- Early identification and remediation of security vulnerabilities.
Why do we recommend it?
GitLab offers reliable static code analysis capabilities integrated into the development process, helping organizations identify and address code vulnerabilities efficiently.
Who is it recommended for?
Recommended for organizations seeking a comprehensive static code analysis tool for improving code quality and security.
Pros:
- Effective vulnerability analysis.
- Integration with CI/CD pipelines and ticketing systems.
- Easy integration with IDE and detailed error mitigation guidance.
Cons:
- Lack of enterprise features.
- Challenges with integration into product infrastructure.
Pricing:
GitLab offers a range of pricing plans to suit different needs. The Free plan is perfect for personal projects and small businesses, with no cost per user and no credit card required. It includes features like 5 GB storage, 10 GB transfer per month, and 400 compute minutes per month. For scaling organizations, the Premium plan, priced at $29 per user per month (billed annually), offers additional features such as Code Ownership, Advanced CI/CD, and 50 GB storage. Enterprises looking for comprehensive security and compliance can opt for the Ultimate plan, which includes everything from Premium along with features like Dynamic Application Security Testing and Portfolio Management.
Circle CI
Circle CI’s continuous integration and continuous delivery (CI/CD) platform optimizes test execution with parallelism support, enhancing efficiency in supply chain management.
Key Features:
- Continuous integration and continuous delivery (CI/CD) platform.
- Parallelism support for efficient test execution.
- Insights and monitoring for identifying and resolving issues quickly.
Why do we recommend it?
Circle CI offers a robust CI/CD platform with parallelism support and insightful monitoring features, ideal for organizations seeking efficient and reliable automation.
Who is it recommended for?
Recommended for teams looking to streamline their CI/CD pipelines with efficient parallel testing and comprehensive insights into build performance.
Pros:
- Ease of setup and implementation.
- insights and monitoring features enable quick issue identification and resolution
- Enough info provided for thorough understanding test failures.
Cons:
- Occasional connectivity issues affecting reliability.
- Complexity in billing and usage tracking.
Pricing:
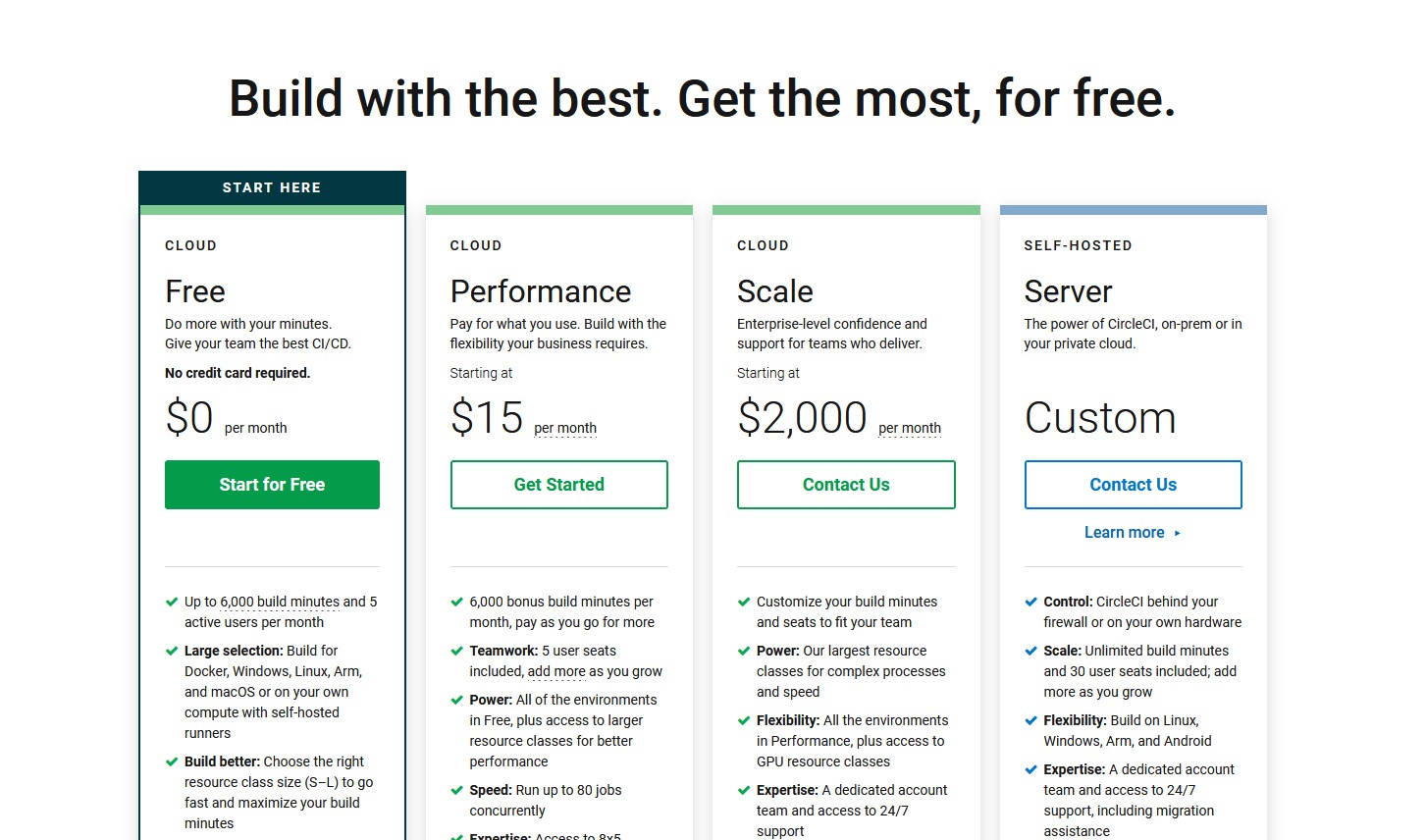
CircleCI offers flexible pricing plans to meet different business needs. The Cloud Free plan provides up to 6,000 build minutes and 5 active users per month. The Performance plan, starting at $15 per month, offers 6,000 bonus build minutes, larger resource classes, and support for up to 80 concurrent jobs. For enterprise-level confidence, the Scale plan, starting at $2,000 per month, allows customization of build minutes and seats, access to GPU resource classes, and dedicated account support.
Crowdstrike
CrowdStrike’s supply chain management tool offers effective threat detection capabilities, utilizing advanced behavioral-based analysis to identify and mitigate supply chain attacks efficiently. By integrating real-time threat intelligence, the tool empowers organizations to adopt proactive defense strategies, staying ahead of emerging threats and providing context-rich information for informed decision-making.
CrowdStrike provides proactive services such as Cybersecurity Maturity Assessment and tabletop exercises, enabling organizations to assess their current exposure and enhance their readiness against supply chain attacks.
Key Features:
- Behavioral-based Attack Detection: Utilizes behavioral analysis, including indicators of attack (IOAs), to detect sophisticated supply chain attacks.
- Threat Intelligence Integration: Provides real-time threat intelligence to identify emerging supply chain threats and proactively defend against them.
- Proactive Services: Offers proactive services such as Cybersecurity Maturity Assessment and tabletop exercises to assess and enhance protection against supply chain attacks.
Why Do We Recommend It?
CrowdStrike’s supply chain management tool offers effective threat detection capabilities, utilizing advanced behavioral-based analysis to identify and mitigate supply chain attacks efficiently. By integrating real-time threat intelligence, the tool empowers organizations to adopt proactive defense strategies, staying ahead of emerging threats and providing context-rich information for informed decision-making. Additionally, CrowdStrike provides proactive services such as Cybersecurity Maturity Assessment and tabletop exercises, enabling organizations to assess their current exposure and enhance their readiness against supply chain attacks.
Who Do We Recommend It For?
This tool is ideal for enterprises seeking comprehensive protection against supply chain threats, especially those with complex supply chains requiring advanced threat detection capabilities and real-time threat intelligence. It is well-suited for organizations prioritizing proactive defense strategies, including behavioral-based analysis and proactive services, to strengthen their resilience against evolving cyber threats.
Pros:
- Advanced Detection Capabilities: Utilizes machine learning and behavioral analysis to detect patterns indicative of supply chain attacks.
- Real-time Threat Intelligence: Employs threat intelligence to stay ahead of emerging threats and provide context-rich information for proactive defense.
Cons:
- Dependency on Behavioral Analysis: Relies heavily on behavioral-based attack detection, which may not be foolproof against all types of supply chain attacks.
- Complexity for Users: Requires users to understand and navigate the complexities of supply chain risk management, including the interpretation of threat intelligence and implementation of proactive measures.
Pricing:
CrowdStrike offers Falcon® bundles tailored to meet different business needs and budgets. The Falcon Go package, priced at $59.99 per year, provides next-gen antivirus protection, device control, and express support. Falcon Pro, at $99.99 per device annually, offers superior protection, integrated threat intelligence, and firewall management. Falcon Enterprise, priced at $184.99 per device per year, includes Falcon Pro features plus EDR and threat hunting. Falcon Elite, with advanced visibility and threat prevention, requires contacting sales for pricing.
Docker
Docker accelerates application building, testing, and deployment by packaging software into standardized units called containers. It simplifies code deployment with a standard execution environment, installed on each server, providing straightforward commands for managing containers.
Key Features:
- Standardized application deployment through containerization.
- Portability ensures consistent performance across various environments.
- Resource optimization with Docker containers.
- Enhanced productivity with simple syntax.
Why do we recommend it?
Docker offers a robust solution for accelerating software delivery, standardizing operations, and optimizing resource utilization.
Who is it recommended for?
Recommended for organizations aiming to increase deployment frequency, standardize operations, and save costs on infrastructure.
Pros:
- Accelerated software delivery with frequent code shipping.
- Streamlined deployment and issue resolution with containerized applications.
- Seamless code migration from development to production environments.
- Cost savings through optimized resource utilization.
Cons:
- Learning curve for new users, especially with Docker’s command-line interface.
- Potential resource overhead when running Docker on each server.
- Security requires proper configuration and ongoing management.
Pricing:
Docker offers a range of subscription plans tailored to meet the needs of developers and businesses, each with distinct features and pricing tiers. The Personal plan is designed for new developers and students and is available at no cost. The Pro plan, ideal for professional developers, offers additional features such as unlimited private repositories and increased image pulls per day for $5 per month. The Team plan provides features like role-based access control and audit logs for $9 per user per month. Businesses aiming for an enterprise-grade development approach can opt for the Business plan, which includes hardened Docker Desktop and single sign-on (SSO) for $24 per user per month.
Wiz
Wiz provides a comprehensive cloud security suite, offering visibility into cloud assets and security posture. With automation and integration capabilities, it strengthens operational efficiency in supply chain risk management, ensuring resilience across cloud-based supply chains.
Key Features:
- Cloud security suite with various solutions consolidated into a single platform.
- Extensive visibility into cloud assets and security posture.
- Automation and integration capabilities for operational efficiency.
Why do we recommend it?
Wiz offers a comprehensive cloud security solution with user-friendly features and strong customer support, suitable for organizations prioritizing cloud security and automation.
Who is it recommended for?
Recommended for organizations seeking a consolidated platform for cloud security management with automation capabilities and responsive support.
Pros:
- Comprehensive cloud security functionalities.
- User-friendly interface for quick access to critical information.
- Responsive customer support for prompt assistance.
- Continuous innovation with new features and updates.
Cons:
- Learning curve for navigating the platform.
- Challenges with support availability based on location.
- Complexity in analyzing and organizing data.
- Limited customization options in certain areas.
Pricing:
Wiz does not have publicly available pricing. In order to learn more about pricing, you’ll have to submit some basic info about your company and Wiz will generate a quote.
TrustInSoft Analyzer
TrustInSoft Analyzer offers formal verification for identifying software vulnerabilities, essential for securing the digital supply chain. Its thorough analysis ensures code integrity, mitigating risks associated with vulnerable software components.
Key Features:
- Formal verification tool for identifying software vulnerabilities.
- Thorough analysis ensuring code integrity and security.
Why do we recommend it?
TrustInSoft Analyzer offers a convenient solution for identifying software vulnerabilities through formal verification, ensuring code integrity and security.
Who is it recommended for?
Recommended for organizations seeking a tool for thorough analysis and identification of software vulnerabilities.
Pros:
- Identifies both common and severe threat categories and coding errors before deployment
- User-friendly interface makes it accessible for ordinary software developers
- Helpful in maintaining a secure development environment.
Cons:
- The need to replace the local self-developed LIBC library during verification can render the library unverifiable
- Difficulty verifying certain common “if” comparisons and loops
Pricing:
Pricing information for TrustInSoft’s supply chain software could not be found online. Based on reviews, it seems that the company is less flexible about pricing than competitors like JFrog.
Hdiv Detection SCA (Datadog)
The Hdiv Detection SCA tool features an intuitive interface for easy use by engineers, facilitating vulnerability identification and remediation. With advanced scanning techniques, Hdiv Detection SCA ensures exceptional accuracy in identifying potential threats across supply chains.
Key Features:
- Platform for identifying and preventing security vulnerabilities in the development process.
- Enhances the overall security posture of software applications.
Why do we recommend it?
Hdiv Detection offers a powerful platform for identifying and preventing security vulnerabilities, enhancing the security of software applications.
Who is it recommended for?
Recommended for organizations prioritizing application security and seeking a tool for comprehensive vulnerability detection and prevention.
Pros:
- Effective platform for identifying and preventing vulnerabilities.
- Improves the overall security posture of applications.
Cons:
- Significantly higher price point than other tools in the space
Pricing:
Regarding pricing, while specifics are unavailable, Datadog’s offerings typically target enterprise-level customers. Despite potentially higher costs, the tool’s advanced capabilities and security level make it valuable for organizations with robust security needs and budgets to accommodate premium solutions. Datadog’s Hdiv Detection SCA’s premium nature may not suit organizations with low annual revenue.
Snyk
Snyk offers real-time vulnerability detection and remediation advice, empowering developers to secure code as it’s being written. Additionally, the tool provides support for industry-standard software bill of materials (SBOM) formats, ensuring transparency and compliance.
Key Features:
- Snyk Code (SAST): Secure code as it’s written with real-time SAST protection.
- Snyk Open Source (SCA): Avoid vulnerable dependencies by tracking over 1 million open source packages across ecosystems.
- Snyk Container: Keep base images secure by analyzing container images and providing fix advice.
- Snyk Infrastructure as Code: Fix misconfigurations in the cloud with automated security checks.
- Snyk AppRisk (ASPM): Reduce risk across the business with comprehensive vulnerability data and guided security.
- Snyk CLI: Run locally or in CI/CD pipelines to scan projects for security issues, including vulnerabilities and license problems.
Why do we recommend it?
Snyk offers real-time vulnerability detection and remediation advice, empowering developers to secure code as it’s being written. Additionally, the tool provides support for industry-standard software bill of materials (SBOM) formats, ensuring transparency and compliance.
Who is it recommended for?
Snyk is particularly beneficial for development teams seeking to secure critical components of their software supply chain, including code, dependencies, containers, and infrastructure. It is suitable for both small development teams and large enterprises looking to mitigate security risks effectively.
Snyk’s developer-first approach and integration into existing development workflows make it accessible and valuable for developers, security professionals, and DevOps teams alike.
Pros:
- Comprehensive coverage of critical components in the software supply chain, including code, dependencies, containers, and infrastructure.
- Support for industry-standard software bill of materials (SBOM) formats, ensuring transparency and compliance.
- Developer-first approach. Integration with various tools, pipelines, and workflows, enables security throughout the supply chain.
Cons:
- May require some learning curve for new users to fully utilize all features.
- Some advanced features may require additional configuration or setup.
- Limited customization options in certain areas may not meet the specific needs of all organizations. Can be hard to scale based on complexity.
Pricing:
Snyk offers a range of pricing plans tailored to meet the diverse needs of developers and organizations. The Free plan is ideal for individual developers and small teams, providing essential security features at no cost. It includes unlimited contributing developers but has limitations on the number of tests per product.
For development teams seeking to integrate security into their workflow, the Team plan starts at $25 per month per product. Additionally, organizations looking to standardize developer-first security practices can opt for the Enterprise plan, which offers centralized policy governance. For pricing details on the Enterprise plan, interested parties can contact the sales team.
Conclusion
By investing in supply chain risk management tools and implementing best practices for supply chain security, organizations can reduce the likelihood and impact of supply chain cyberattacks, safeguarding their assets, reputation, and customer trust. With the right tools and strategies in place, organizations can navigate the complex landscape of supply chain cybersecurity with confidence
The 10 tools listed above offer a range of features and capabilities to help organizations manage supply chain risk effectively. Whether it’s managing software artifacts, conducting vulnerability assessments, or streamlining development processes, these tools can help organizations enhance their cybersecurity posture and protect against supply chain cyberattacks.
Among these tools, JFrog stands out as the Editor’s Pick for its comprehensive software supply chain management platform, secure artifact management, and vulnerability scanning capabilities. With easy deployment, maintenance, and detailed scan results, JFrog offers a robust solution for managing software artifacts and dependencies throughout the development lifecycle, with strong security features and comprehensive vulnerability scanning. The built-in JFrog Academy education platform is one of the more robust educational modules offered by players in this space.