Every organization today handles sensitive data, which could include the Personally Identifiable Information (PII) of employees and end-customers, financial details, intellectual properties of the organization, and anything else that can have serious consequences when viewed by unauthorized users. Due to this potential impact on user privacy and security, organizations are using multiple strategies to safeguard them. Moreover, many governments are laying down stringent rules on the storage, handling, and usage of sensitive data, and organizations are forced to take measures to comply with these laws.
Below are the ten best DLP software:
- Forcepoint DLP – An enterprise solution that protects your data stored on-premises and in the cloud. Also, it discovers, classifies, and protects data from using its risk-adaptive protection.
- Endpoint Protector – A comprehensive platform for protecting endpoint devices running Windows, Linux, and macOS operating systems. It also helps to control USB and peripheral port devices.
- Digital Guardian Endpoint DLP – A DLP tool that identifies and protects a wide range of data types, including unstructured data. It secures the end devices through which data can likely leave your organization.
- Checkpoint DLP – A 360-degree visibility and reporting tool that monitors sensitive data and detects data losses as they happen in real-time.
- Symantec DLP- An information security platform that offers the required protection to prevent data loss and non-compliance.
- Trend Micro Integrated DLP – A lightweight platform that safeguards your digital assets from accidental or deliberate data loss.
- Proofpoint Enterprise DLP – A unified tool that protects data across emails, cloud, and endpoints to protect data breaches across multiple scenarios.
- Trellix DLP – A platform to discover, identify, classify, monitor, and protect data through a single platform. It can be deployed on-premises or on the cloud.
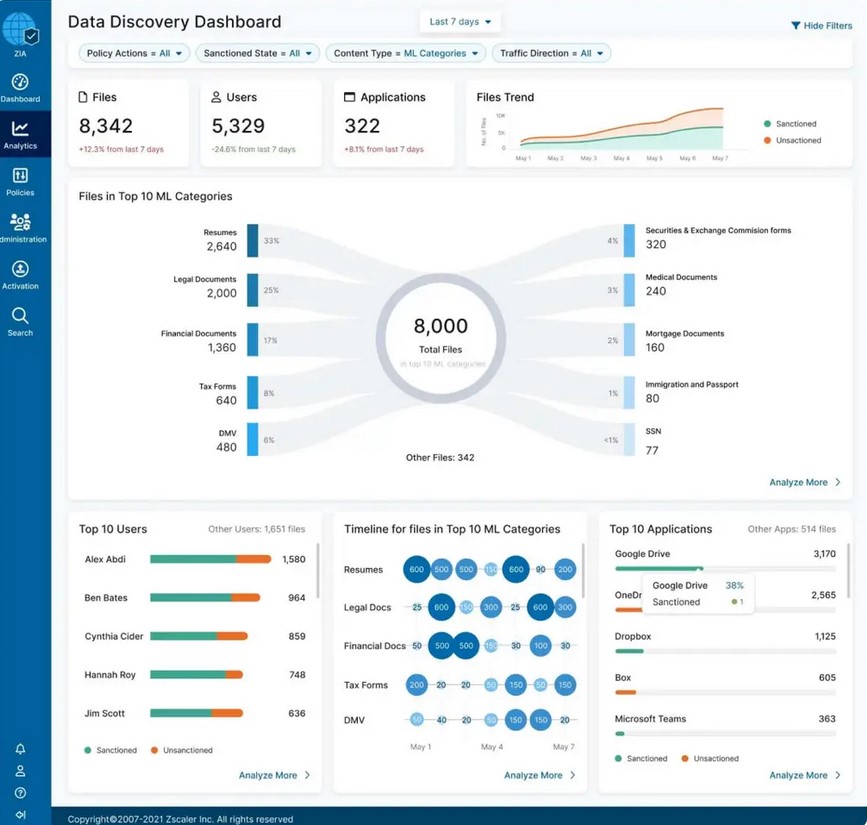
- Zscaler DLP – A modern platform that monitors and blocks data to protect it from unauthorized use or loss.
- Palo Alto Networks Enterprise DLP – A cloud-sensitive DLP that protects data across networks, clouds, and users.
One such strategy is Data Loss Prevention (DLP), where organizations use advanced tools to monitor user access to sensitive data, to prevent them from misuse, theft, or accidental loss. These DLP tools classify data automatically and ensure that its usage meets your organization’s security and access policies. Some tools even notify of non-compliance with your internal policies as well as leading regulations like GDPR. Furthermore, they prevent data loss from insider threats and accidental mishandling.
The key is to choose the right DLP tool that best fits your needs, and in the article, we have identified the top ten data loss prevention software for you.
Our Methodology
We evaluated the DLP tools based on the below criteria:
- Efficiency in data discovery and classification.
- The availability of policy templates for data handling.
- Extensive customization options.
- Analytics and reporting.
- Use of contextual information to check for monitoring and compliance.
- Customer support and availability of training videos and documentation.
Best Data Loss Prevention Software
Next, let’s take a detailed look at each tool.
1. Forcepoint DLP
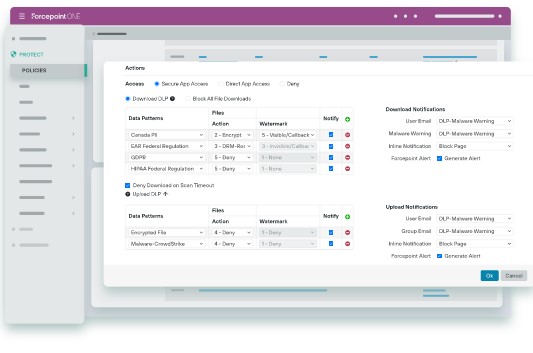
Forcepoint DLP is an enterprise DLP tool that discovers, classifies, monitors, and protects sensitive data handled within your organization. It provides the tools required to formulate and manage policies to prevent data loss across multiple channels.
Source: Forcepoint
Let’s now look at Forcepoint’s important features.
Comprehensive Data Security
With Forcepoint, you can create a comprehensive data security policy and apply it to the data stored anywhere in your organization. You can even extend the policies to your web, cloud, and private applications with just a few clicks. More importantly, you can update policies and they will automatically apply to all data.
Meeting Compliance
If your organization has to comply with different standards, Forcepoint can ease this process for you, as it comes with one of the largest pre-defined policy libraries. You can use any of these templates to ensure compliance with more than 80+ countries’ policies including GDPR, CCPA, and more.
Risk Adaptive Protection
A highlight of Forcepoint is its risk-adaptive protection that detects the risk level of the source based on an individual’s behavior patterns. Accordingly, it formulates an action plan to prevent data breaches. In particular, this strategy helps to prevent insider threats.
Overall, Forcepoint DLP comes with many advantages to classifying, storing, and streamlining access to sensitive data.
Pros:
- Training videos and documentation are available.
- Modular and flexible.
- Extensive filtering and customization options.
- Seamless integration.
Cons:
- No protection during file transfers.
- Customer support can be better.
2. Endpoint Protector
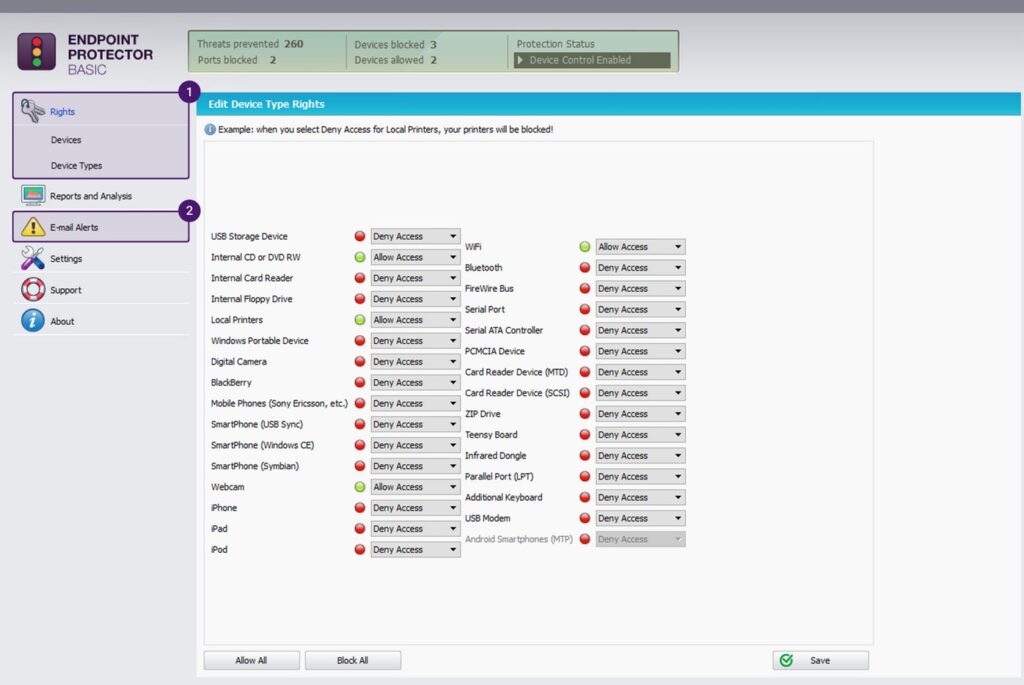
Endpoint Protector is a DLP tool that works well across Windows, Linux, and macOS devices to discover, monitor, and protect your sensitive data. It also continuously monitors all USB and peripheral port devices to safeguard your data.
Source: Endpoint Protector
Below is a look at Endpoint Protector’s features.
Content-Aware Data Protection
Endpoint Protector uses content inspection and contextual scanning to protect your sensitive data from unauthorized access and sharing. It also prevents employees from exfiltrating sensitive data through USB devices, Bluetooth connections, and more. The advantage is that these policies offer continuous protection even when employees are offline.
USB Encryption
The data stored on USB devices is encrypted to protect data during transit. It uses AES 256-bit encryption to protect your data from loss or theft, regardless of the device in which it is stored. More importantly, this enforced encryption enables organizations to comply with regulations like NIST, HIPAA, and more.
Granular Control
With Endpoint Protector, you can have granular control over the devices that connect to your USB and peripheral ports. You can remotely monitor these devices regardless of the operating system to which they connect. Also, you can track these devices by their vendor ID, serial number, and more.
Due to these features, Endpoint Protector can provide overarching protection to your sensitive data, regardless of where they are stored.
Pros:
- Extensive policies and implementation.
- Granular control and visibility.
- Flexible deployment.
- Highly compatible with popular operating systems.
Cons:
- No option for web filtering.
- Limited integrations.
3. Digital Guardian Endpoint DLP
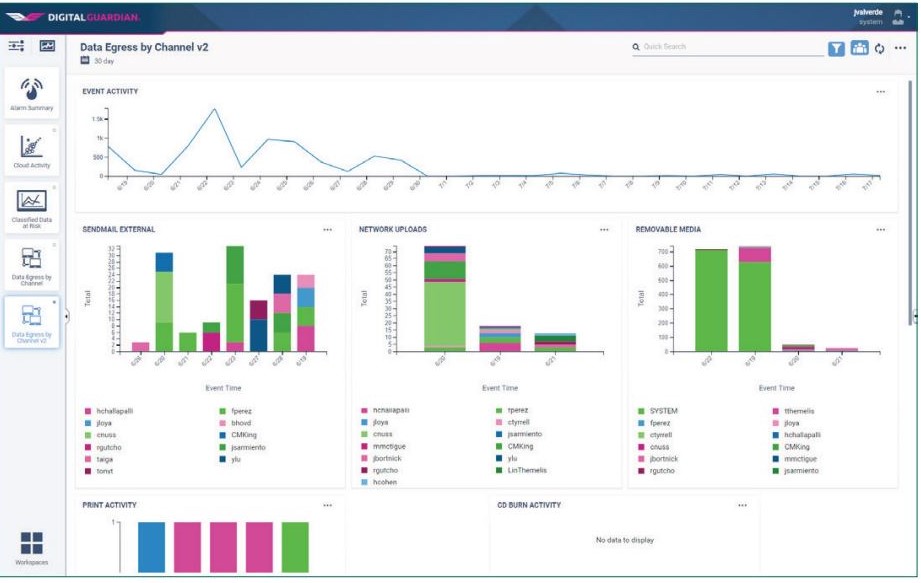
The Digital Guardian Endpoint DLP uses agents to capture and record all system, user, and data events that happen on endpoints to prevent sensitive data from leaving your organization. Moreover, it scans all data types, including unstructured data, to identify sensitive information and protect it.
Source: Digital Guardian
Here’s a peek into Digital Guardian’s features.
Automated Classification
You must identify and classify sensitive data before protecting it, and this can be an arduous process. Digital Guardian offers automated classification of data to save time and effort. This identification starts right after you install the tool, and doesn’t require any specialized instructions.
Support Across Devices
Digital Guardian protects the sensitive data located on Windows, Linux, and macOS end devices. It can also monitor structured and unstructured data running on multiple systems, both on and off networks. It also provides complete control and visibility over your data and its access.
Extensive Dashboard
Another salient aspect of this tool is the out-of-the-box dashboards. You can customize them to meet your specific needs and views, and get the required information for further processing and decision-making. It can also help with decision-making,
Overall, Digital Guardian is a DLP tool for gaining the in-depth visibility you require to ensure that your sensitive information is not sent to other devices.
Pros:
- Comprehensive classification, regardless of where you send your sensitive data.
- Excellent customer support.
- Monitors data transfer across vectors.
- Robust data classification
Cons:
- It can consume considerable device resources.
- Limited integrations.
4. Checkpoint DLP
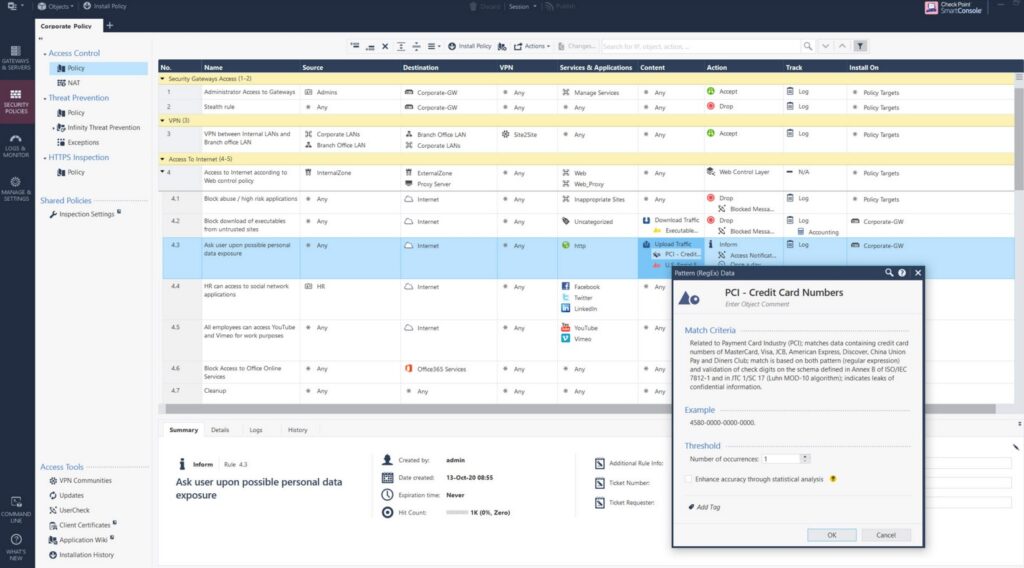
Checkpoint DLP proactively protects your sensitive data and prevents it from intentional and accidental data loss. It integrates with Checkpoint’s Next Generation Firewall (NGFW) to monitor the movement of your sensitive data and ensure that it doesn’t leave your organization through unauthorized channels.
Source: Checkpoint
Below are Checkpoint’s DLP features.
Custom Data Types
Checkpoint supports 500+ predefined data types. Moreover, you can customize each of these data types with keywords, file attributes, and more to define the data type you need. You can even use regular expressions and patterns to ensure your sensitive data fits into a specific data type for protection.
Comprehensive Reporting
With Checkpoint, you can get 360-degree visibility into your data movement and location. It also integrates with SmartEvent, using which you can decide what kind of notifications you need and when. You can also leverage its reporting capabilities to create custom reports that are highly beneficial for your decision and policy-making.
Awareness and Education
Checkpoint continuously educates your end-users about the proper data handling to reduce the burden on your IT teams. More importantly, it sends alerts to the relevant users when there are violations of existing policies.
In all, Checkpoint enables your employees to confidently work with data, protects your sensitive information, and ensures compliance with the relevant standards.
Pros:
- Highly customizable.
- Real-time monitoring and reporting.
- Projects sensitive information on web browsers and emails.
- Robust administrative controls.
Cons:
- Configuration can be complex.
- Impact on system performance.
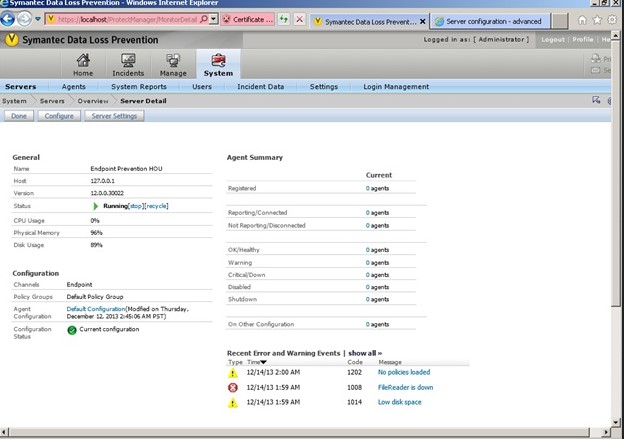
5. Symantec DLP
Symantec DLP, a part of Broadcom, is an information security platform that comes with advanced features like improved detection and workflow changes to monitor your data in real-time and protect it from likely breaches. It offers all the visibility you need from a single control point.
Source: Symantec
Let’s understand what Symantec can do for you.
Multi-channel Support
Symantec DLP protects your data across multiple channels like email, cloud apps, external storage devices, virtual desktops, servers, laptops, and more. It acts as a central point to ensure that there are no data leaks across all your channels.
Protection of Data in Transit
The use of many collaboration tools coupled with a remote workforce puts sensitive data at risk. To avoid intentional and accidental data leaks, Symantec captures and analyzes all outbound traffic to detect sensitive content and metadata. If it identifies any potential for data leaks, Symantec DLP alerts the concerned teams/individuals.
Protection for Data at Rest
A highlight of Symantec DLP is that it identifies the sensitive data stored on files, endpoint devices, network file shares, databases, SharePoint, and other data repositories. It can even protect data stored in the cloud from unauthorized access or transfer.
Overall, Symantec DLP protects data across any point or device in your network.
Pros:
- Monitor data across emails, web browsers, storage devices, and more.
- Protects against data loss due to human errors.
- Easy to implement security policies.
- Highly scalable.
Cons:
- Initial configuration can be cumbersome.
- API integration is difficult.
6. Trend Micro Integrated DLP
Using Trend Micro Integrated DLP, you can identify what digital assets to protect and create policies to limit their transmission through channels like email and other external devices. Moreover, it is lightweight and provides control and visibility into your sensitive data.
Source: Trend Micro
Here’s a look at Trend Micro Integrated DLP’s features.
Data Control
Trend Micro offers granular device control, including the option to create specific policies and rules based on the vendor ID or the serial number of a device. It also analyzes keywords, regular expressions, and file attributes to identify improper data use, and reports them right away. Moreover, this tool makes it easy for IT teams to prevent data transfer through USB and other portable devices.
Compliance
With its out-of-the-box compliance templates, Trend Micro ensures that you can meet the obligation of most regulations. It also speeds up the internal audit process while supporting actions with forensic data. It even generates real-time reports.
Streamlined Administration
Trend Micro is a lightweight tool that simplifies deployment and overall administration. More importantly, it requires fewer resources to execute when compared to many DLP tools. Its unified dashboard also enhances your visibility and control of how sensitive data moves through your organization.
In all, Trend Micro is a handy DLP tool that protects your sensitive data while reducing administrative costs and complexity.
Pros:
- Simple to set up.
- Easy compliance with HIPAA and other standards.
- Fewer resource usage.
- Integrates well with other Trend Micro tools.
Cons:
- Limited advanced features
- False positives.
7. Proofpoint Enterprise DLP
Proofpoint DLP takes a people-centric approach to DLP where it ensures that data losses and breaches do not happen due to human behavior. It combines content, behavior, and telemetry across multiple channels like email, cloud, and endpoint to create people-oriented data loss scenarios. Accordingly, it protects your organization from these scenarios.
Source: Proofpoint
Here’s a look at Proofpoint’s DLP capabilities.
Focus on Security and Compliance
This tool uses behavior, content, and telemetry on a single timeline to help you get a contextual awareness of the threats. It also helps you determine the intent behind people’s actions and the risks involved. With this view, you can better understand if a specific user is compromised or malicious.
Common DLP Policies
Proofpoint comes with many common DLP policies and templates. With more than 240 customizable templates, you can classify sensitive data from almost any source. It also offers support to OCR for gathering the sensitive data in your images.
Unified Interface
Proofpoint offers a unified alert and investigations interface that enables you to respond quickly to security issues. Also, you have the option to include encryption to suspect emails and even shut down any cloud account that you find compromised.
With such features, Proofpoint can protect your data and ensure that your policies are in tune with your people and processes.
Pros:
- Option for email encryption.
- Highly customizable rules.
- Easy to implement.
- Makes sense of telemetry data.
Cons:
- Limited training and documentation.
- Limited focus on web browsing.
8. Trellix DLP
Trellix DLP safeguards your organization from accidental and intentional data leakage. At the same time, it complies with regulatory standards and helps ensure that your sensitive information is always protected.
Source: Trellix
Let’s see how Trellix DLP can protect your data.
Wide Range of Content
Trellix supports more than 400 content types, and this means, sensitive data in any form can be identified and classified easily. Regardless of the data type, you can create security policies and implement them uniformly. The advantage of such uniform policies is that you have comprehensive control over every piece of sensitive data, and can even decide when it requires added protection.
Anomaly Detection
This tool scans and analyzes your network data in real-time to prevent data loss and even mitigate its impact. It also supports many protocols like SMTP, Telnet, LDAP, and more. With such continuous monitoring, it can also detect anomalies in data transmission.
Email Handling
Trellix can quarantine, encrypt, or block emails depending on their content. It also enables email administrators to apply the organization’s security policies to prevent users from sending unauthorized information.
Pros:
- Automated reporting.
- Supports the use of common policies
- Searches for sensitive information and safeguards it.
- Tracks data transmission.
Cons:
- Limited tutorials.
- Does not integrate well with all leading tools.
9. Zscaler DLP
Zscaler DLP is a modern and simple platform for defending your data from potential loss. It protects data and blocks it when required to ensure that it is not accessed by unauthorized users. Moreover, it acts as a central point to protect all your data, regardless of where they are located.
Source: Zscaler
Read on to learn Zscaler’s DLP capabilities.
Streamlined Security
The high-performance cloud inspects all Internet and SSL to provide streamlined and consistent security across all your assets. Moreover, Zscaler DLP integrates well with Zscaler’s Zero Trust Exchange to eliminate the costs and complexity of data protection.
Data Discovery
Zscaler uses an advanced feature called Zero Configuration Data Protection (ZCDP) to automatically discover and categorize data. With such a unified approach to data discovery, you get actionable insight and visibility across all your data storage. Moreover, you can easily find sensitive data and implement security controls on them.
Advanced Features
Besides data discovery, Zscaler also comes with other advanced features that improve data occurrence. Specifically, it fingerprints sensitive data while reducing false positives. Moreover, its IDM capabilities protect the sensitive data contained in documents while the OCR tool detects and safeguards data in images.
Overall, Zscaler can help you defend sensitive data from thefts and losses.
Pros:
- Easy to find and classify sensitive data.
- Straightforward initial setup.
- Highly scalable
- Integrates well with other platforms.
Cons:
- Limited support for audio and video Internet traffic.
- No machine learning or AI automation.
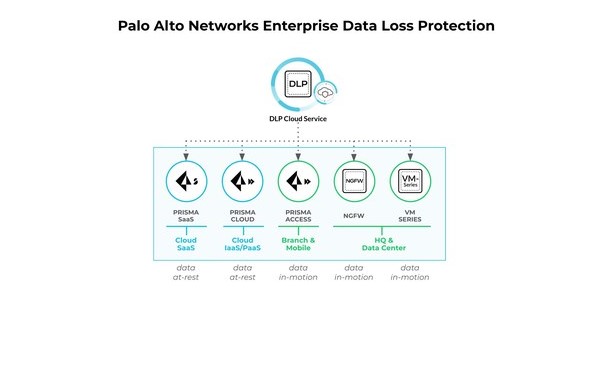
10. Palo Alto Networks Enterprise DLP
The Palo Alto Networks Enterprise DLP is a cloud-based solution that protects the sensitive data located across networks, users, and cloud infrastructure. With such a concerted approach, it prevents data breaches and the resulting reputation of the company. Moreover, it helps you comply with standards like PCI-DSS, HIPAA, and more.
Source: Palo Alto Networks
Let’s look at the DLP capabilities of Palo Alto Networks.
Simplified Operations
This tool discovers, monitors, and protects sensitive data to match every scenario. Its well-designed templates support customization and can help ensure data privacy and security across your entire infrastructure. It also integrates well with any tech stack to simplify your daily operations.
Automatic Detection
Palo Alto Networks DLP automatically identifies sensitive information, even if they are present within images, documents, unstructured conversations on collaboration apps like Slack, and more. Such seamless detection provides higher control with minimal effort.
Data Protection
This DLP solution integrates well with other Palo Alto Networks products to cover SaaS applications, public clouds, and more. Its integrations with NGFW, VM-Series, emails, CASB, and even generative AI apps make it highly relevant for today’s evolving technological environment.
Overall, Palo Alto Networks provides comprehensive data protection and security for your organization.
Pros:
- Ideal for a remote workforce.
- Works well for SaaS applications and public clouds.
- Setup is easy.
- Good reporting capabilities.
Cons:
- Closely knit with other Palo Alto Network products.
- Documentation and training can be better.
These are our top 10 DLP tools. As you can see, they are not alike though they have some overlapping features. Make sure to pick a tool that best fits your organization’s needs.
Final Thoughts
Data loss is a nightmare for organizations because it often leads to financial loss, including expensive lawsuits. Moreover, the organization can end up paying heavy fines, especially if it has to comply with standards like HIPAA and GDPR. Above everything, there’s a loss of trust in the organization’s operations, leading to severe reputational loss.
To avoid these repercussions, organizations use multiple strategies, and data loss prevention is one of them. In this article, we discussed ten tools that can monitor the movement of your sensitive data and prevent data loss due to human errors. We hope this information comes in handy to select the appropriate tool.